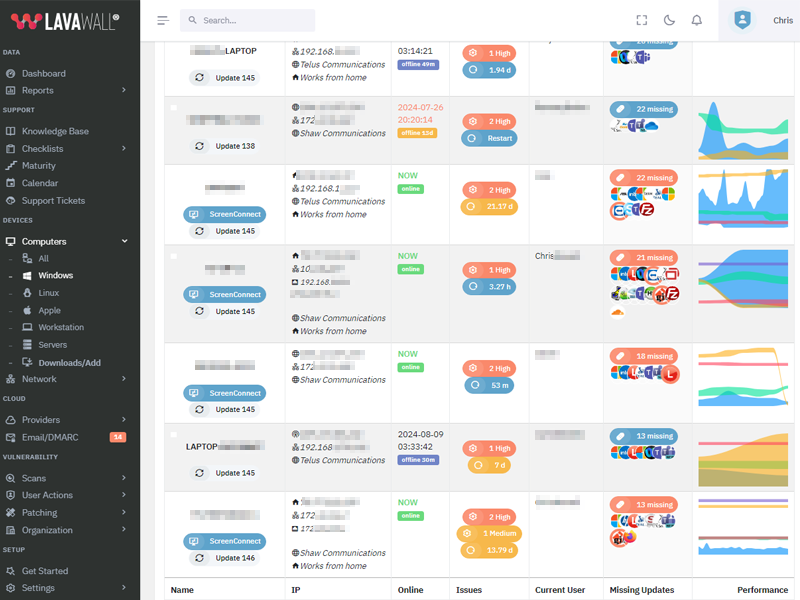
Update ChromeOS Platform to version 15964.48.0
What patches are you missing?
CVE Vulnerabilities for ChromeOS Platform
| CVE | Published | Severity | Details | Exploitability | Impact | Vector |
| CVE‑2023‑4369 | 2023‑08‑15 18:15:14 | HIGH (9) | Insufficient data validation in Systems Extensions in Google Chrome on ChromeOS prior to 116.0.5845.120 allowed an attacker who convinced a user to install a malicious extension to bypass file restrictions via a crafted HTML page. (Chromium security severity: Medium) | 3 | 6 | NETWORK |
| CVE‑2023‑3742 | 2023‑12‑20 16:15:09 | MEDIUM (7) | Insufficient policy enforcement in ADB in Google Chrome on ChromeOS prior to 114.0.5735.90 allowed a local attacker to bypass device policy restrictions via physical access to the device. (Chromium security severity: High) | 1 | 6 | PHYSICAL |
| CVE‑2023‑3739 | 2023‑08‑01 23:15:34 | MEDIUM (6) | Insufficient validation of untrusted input in Chromad in Google Chrome on ChromeOS prior to 115.0.5790.131 allowed a remote attacker to execute arbitrary code via a crafted shell script. (Chromium security severity: Low) | 3 | 3 | NETWORK |
| CVE‑2023‑3731 | 2023‑08‑01 23:15:32 | HIGH (9) | Use after free in Diagnostics in Google Chrome on ChromeOS prior to 115.0.5790.131 allowed an attacker who convinced a user to install a malicious extension to potentially exploit heap corruption via a crafted Chrome Extension. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2023‑3729 | 2023‑08‑01 23:15:32 | HIGH (9) | Use after free in Splitscreen in Google Chrome on ChromeOS prior to 115.0.5790.131 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interactions. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2023‑3497 | 2023‑07‑03 17:15:10 | MEDIUM (5) | Out of bounds read in Google Security Processor firmware in Google Chrome on Chrome OS prior to 114.0.5735.90 allowed a local attacker to perform denial of service via physical access to the device. (Chromium security severity: Medium) | 1 | 4 | PHYSICAL |
| CVE‑2023‑2461 | 2023‑05‑03 00:15:09 | HIGH (9) | Use after free in OS Inputs in Google Chrome on ChromeOS prior to 113.0.5672.63 allowed a remote attacker who convinced a user to enage in specific UI interaction to potentially exploit heap corruption via crafted UI interaction. (Chromium security severity: Medium) | 3 | 6 | NETWORK |
| CVE‑2023‑2458 | 2023‑05‑12 18:15:10 | HIGH (9) | Use after free in ChromeOS Camera in Google Chrome on ChromeOS prior to 113.0.5672.114 allowed a remote attacker who convinced a user to engage in specific UI interaction to potentially exploit heap corruption via UI interaction. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2023‑2457 | 2023‑05‑12 18:15:10 | HIGH (9) | Out of bounds write in ChromeOS Audio Server in Google Chrome on ChromeOS prior to 113.0.5672.114 allowed a remote attacker to potentially exploit heap corruption via crafted audio file. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2023‑0137 | 2023‑01‑10 20:15:11 | HIGH (9) | Heap buffer overflow in Platform Apps in Google Chrome on Chrome OS prior to 109.0.5414.74 allowed an attacker who convinced a user to install a malicious extension to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: Medium) | 3 | 6 | NETWORK |
| CVE‑2023‑0128 | 2023‑01‑10 20:15:11 | HIGH (9) | Use after free in Overview Mode in Google Chrome on Chrome OS prior to 109.0.5414.74 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑4176 | 2022‑11‑30 00:15:10 | HIGH (9) | Out of bounds write in Lacros Graphics in Google Chrome on Chrome OS and Lacros prior to 108.0.5359.71 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via UI interactions. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑3659 | 2022‑11‑01 23:15:19 | HIGH (9) | Use after free in Accessibility in Google Chrome on Chrome OS prior to 107.0.5304.62 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via specific UI interactions. (Chromium security severity: Medium) | 3 | 6 | NETWORK |
| CVE‑2022‑3658 | 2022‑11‑01 23:15:19 | HIGH (9) | Use after free in Feedback service on Chrome OS in Google Chrome on Chrome OS prior to 107.0.5304.62 allowed an attacker who convinced a user to install a malicious extension to potentially exploit heap corruption via specific UI interaction. (Chromium security severity: Medium) | 3 | 6 | NETWORK |
| CVE‑2022‑3318 | 2022‑11‑01 20:15:22 | MEDIUM (4) | Use after free in ChromeOS Notifications in Google Chrome on ChromeOS prior to 106.0.5249.62 allowed a remote attacker who convinced a user to reboot Chrome OS to potentially exploit heap corruption via UI interaction. (Chromium security severity: Low) | 3 | 1 | NETWORK |
| CVE‑2022‑3309 | 2022‑11‑01 20:15:21 | MEDIUM (7) | Use after free in assistant in Google Chrome on ChromeOS prior to 106.0.5249.62 allowed a remote attacker who convinced a user to engage in specific UI gestures to potentially perform a sandbox escape via specific UI gestures. (Chromium security severity: Medium) | 3 | 4 | NETWORK |
| CVE‑2022‑3306 | 2022‑11‑01 20:15:21 | HIGH (9) | Use after free in survey in Google Chrome on ChromeOS prior to 106.0.5249.62 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑3305 | 2022‑11‑01 20:15:21 | HIGH (9) | Use after free in survey in Google Chrome on ChromeOS prior to 106.0.5249.62 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑3201 | 2022‑09‑26 16:15:14 | MEDIUM (5) | Insufficient validation of untrusted input in DevTools in Google Chrome on Chrome OS prior to 105.0.5195.125 allowed an attacker who convinced a user to install a malicious extension to bypass navigation restrictions via a crafted HTML page. (Chromium security severity: High) | 3 | 3 | NETWORK |
| CVE‑2022‑3071 | 2022‑09‑26 16:15:13 | HIGH (9) | Use after free in Tab Strip in Google Chrome on Chrome OS, Lacros prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interaction. | 3 | 6 | NETWORK |
| CVE‑2022‑3052 | 2022‑09‑26 16:15:13 | HIGH (9) | Heap buffer overflow in Window Manager in Google Chrome on Chrome OS, Lacros prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑3051 | 2022‑09‑26 16:15:13 | HIGH (9) | Heap buffer overflow in Exosphere in Google Chrome on Chrome OS, Lacros prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑3050 | 2022‑09‑26 16:15:13 | HIGH (9) | Heap buffer overflow in WebUI in Google Chrome on Chrome OS prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑3049 | 2022‑09‑26 16:15:13 | HIGH (9) | Use after free in SplitScreen in Google Chrome on Chrome OS, Lacros prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑3048 | 2022‑09‑26 16:15:12 | MEDIUM (7) | Inappropriate implementation in Chrome OS lockscreen in Google Chrome on Chrome OS prior to 105.0.5195.52 allowed a local attacker to bypass lockscreen navigation restrictions via physical access to the device. | 1 | 6 | PHYSICAL |
| CVE‑2022‑3043 | 2022‑09‑26 16:15:12 | HIGH (9) | Heap buffer overflow in Screen Capture in Google Chrome on Chrome OS prior to 105.0.5195.52 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑3042 | 2022‑09‑26 16:15:12 | HIGH (9) | Use after free in PhoneHub in Google Chrome on Chrome OS prior to 105.0.5195.52 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑2743 | 2023‑01‑02 23:15:11 | HIGH (9) | Integer overflow in Window Manager in Google Chrome on Chrome OS and Lacros prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific UI interactions to perform an out of bounds memory write via crafted UI interactions. (Chrome security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑2742 | 2023‑01‑02 23:15:11 | HIGH (9) | Use after free in Exosphere in Google Chrome on Chrome OS and Lacros prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via crafted UI interactions. (Chrome security severity: High) | 3 | 6 | NETWORK |
| CVE‑2022‑2620 | 2022‑08‑12 20:15:09 | HIGH (9) | Use after free in WebUI in Google Chrome on Chrome OS prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific user interactions to potentially exploit heap corruption via specific UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑2613 | 2022‑08‑12 20:15:09 | HIGH (9) | Use after free in Input in Google Chrome on Chrome OS prior to 104.0.5112.79 allowed a remote attacker who convinced a user to enage in specific user interactions to potentially exploit heap corruption via specific UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑2609 | 2022‑08‑12 20:15:09 | HIGH (9) | Use after free in Nearby Share in Google Chrome on Chrome OS prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific user interactions to potentially exploit heap corruption via specific UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑2608 | 2022‑08‑12 20:15:09 | HIGH (9) | Use after free in Overview Mode in Google Chrome on Chrome OS prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific user interactions to potentially exploit heap corruption via specific UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑2607 | 2022‑08‑12 20:15:09 | HIGH (9) | Use after free in Tab Strip in Google Chrome on Chrome OS prior to 104.0.5112.79 allowed a remote attacker who convinced a user to engage in specific user interactions to potentially exploit heap corruption via specific UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑2587 | 2022‑08‑12 20:15:09 | CRITICAL (10) | Out of bounds write in Chrome OS Audio Server in Google Chrome on Chrome OS prior to 102.0.5005.125 allowed a remote attacker to potentially exploit heap corruption via crafted audio metadata. | 4 | 6 | NETWORK |
| CVE‑2022‑2296 | 2022‑07‑28 02:15:08 | HIGH (9) | Use after free in Chrome OS Shell in Google Chrome on Chrome OS prior to 103.0.5060.114 allowed a remote attacker who convinced a user to engage in specific user interactions to potentially exploit heap corruption via direct UI interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑1641 | 2022‑07‑26 22:15:11 | HIGH (9) | Use after free in Web UI Diagnostics in Google Chrome on Chrome OS prior to 101.0.4951.64 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via specific user interaction. | 3 | 6 | NETWORK |
| CVE‑2022‑1633 | 2022‑07‑26 22:15:10 | HIGH (9) | Use after free in Sharesheet in Google Chrome on Chrome OS prior to 101.0.4951.64 allowed a remote attacker who convinced a user to engage in specific UI interactions to potentially exploit heap corruption via specific user interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑1489 | 2022‑07‑26 22:15:10 | HIGH (9) | Out of bounds memory access in UI Shelf in Google Chrome on Chrome OS, Lacros prior to 101.0.4951.41 allowed a remote attacker to potentially exploit heap corruption via specific user interactions. | 3 | 6 | NETWORK |
| CVE‑2022‑1311 | 2022‑07‑25 14:15:11 | HIGH (9) | Use after free in shell in Google Chrome on ChromeOS prior to 100.0.4896.88 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑1132 | 2022‑07‑23 00:15:09 | MEDIUM (6) | Inappropriate implementation in Virtual Keyboard in Google Chrome on Chrome OS prior to 100.0.4896.60 allowed a local attacker to bypass navigation restrictions via physical access to the device. | 1 | 5 | PHYSICAL |
| CVE‑2022‑0603 | 2022‑04‑05 00:15:17 | HIGH (9) | Use after free in File Manager in Google Chrome on Chrome OS prior to 98.0.4758.102 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑0308 | 2022‑02‑12 02:15:11 | HIGH (9) | Use after free in Data Transfer in Google Chrome on Chrome OS prior to 97.0.4692.99 allowed a remote attacker who convinced a user to engage in specific user interaction to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2022‑0107 | 2022‑02‑12 00:15:08 | HIGH (9) | Use after free in File Manager API in Google Chrome on Chrome OS prior to 97.0.4692.71 allowed an attacker who convinced a user to install a malicious extension to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2021‑38013 | 2021‑12‑23 01:15:08 | CRITICAL (10) | Heap buffer overflow in fingerprint recognition in Google Chrome on ChromeOS prior to 96.0.4664.45 allowed a remote attacker who had compromised a WebUI renderer process to potentially perform a sandbox escape via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2021‑37964 | 2021‑10‑08 22:15:08 | LOW (3) | Inappropriate implementation in ChromeOS Networking in Google Chrome on ChromeOS prior to 94.0.4606.54 allowed an attacker with a rogue wireless access point to to potentially carryout a wifi impersonation attack via a crafted ONC file. | 2 | 1 | LOCAL |
| CVE‑2021‑30565 | 2021‑08‑03 20:15:09 | HIGH (9) | Out of bounds write in Tab Groups in Google Chrome on Linux and ChromeOS prior to 92.0.4515.107 allowed an attacker who convinced a user to install a malicious extension to perform an out of bounds memory write via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2020‑9746 | 2020‑10‑14 14:15:18 | HIGH (9) | Adobe Flash Player version 32.0.0.433 (and earlier) are affected by an exploitable NULL pointer dereference vulnerability that could result in a crash and arbitrary code execution. Exploitation of this issue requires an attacker to insert malicious strings in an HTTP response that is by default delivered over TLS/SSL. | 3 | 6 | NETWORK |
| CVE‑2020‑9633 | 2020‑06‑12 14:15:11 | CRITICAL (10) | Adobe Flash Player Desktop Runtime 32.0.0.371 and earlier, Adobe Flash Player for Google Chrome 32.0.0.371 and earlier, and Adobe Flash Player for Microsoft Edge and Internet Explorer 32.0.0.330 and earlier have an use after free vulnerability. Successful exploitation could lead to arbitrary code execution. | 4 | 6 | NETWORK |
| CVE‑2020‑6485 | 2020‑05‑21 04:15:14 | MEDIUM (7) | Insufficient data validation in media router in Google Chrome prior to 83.0.4103.61 allowed a remote attacker who had compromised the renderer process to bypass navigation restrictions via a crafted HTML page. | 3 | 4 | NETWORK |
| CVE‑2020‑6381 | 2020‑02‑11 15:15:12 | HIGH (9) | Integer overflow in JavaScript in Google Chrome on ChromeOS and Android prior to 80.0.3987.87 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2020‑3757 | 2020‑02‑13 16:15:13 | HIGH (9) | Adobe Flash Player versions 32.0.0.321 and earlier, 32.0.0.314 and earlier, 32.0.0.321 and earlier, and 32.0.0.255 and earlier have a type confusion vulnerability. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2020‑16038 | 2021‑01‑08 19:15:14 | HIGH (9) | Use after free in media in Google Chrome on OS X prior to 87.0.4280.88 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2020‑16035 | 2021‑01‑08 19:15:14 | HIGH (9) | Insufficient data validation in cros-disks in Google Chrome on ChromeOS prior to 87.0.4280.66 allowed a remote attacker who had compromised the browser process to bypass noexec restrictions via a malicious file. | 3 | 6 | NETWORK |
| CVE‑2020‑16024 | 2021‑01‑08 19:15:13 | CRITICAL (10) | Heap buffer overflow in UI in Google Chrome prior to 87.0.4280.66 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2020‑16022 | 2021‑01‑08 19:15:13 | HIGH (9) | Insufficient policy enforcement in networking in Google Chrome prior to 87.0.4280.66 allowed a remote attacker to potentially bypass firewall controls via a crafted HTML page. | 3 | 6 | NETWORK |
| CVE‑2020‑16021 | 2021‑01‑08 19:15:13 | HIGH (8) | Race in image burner in Google Chrome on ChromeOS prior to 87.0.4280.66 allowed a remote attacker who had compromised the browser process to perform OS-level privilege escalation via a malicious file. | 2 | 6 | NETWORK |
| CVE‑2020‑16020 | 2021‑01‑08 19:15:13 | HIGH (9) | Inappropriate implementation in cryptohome in Google Chrome on ChromeOS prior to 87.0.4280.66 allowed a remote attacker who had compromised the browser process to bypass discretionary access control via a malicious file. | 3 | 6 | NETWORK |
| CVE‑2020‑16019 | 2021‑01‑08 19:15:13 | HIGH (9) | Inappropriate implementation in filesystem in Google Chrome on ChromeOS prior to 87.0.4280.66 allowed a remote attacker who had compromised the browser process to bypass noexec restrictions via a malicious file. | 3 | 6 | NETWORK |
| CVE‑2019‑8075 | 2019‑09‑27 16:15:11 | HIGH (8) | Adobe Flash Player version 32.0.0.192 and earlier versions have a Same Origin Policy Bypass vulnerability. Successful exploitation could lead to Information Disclosure in the context of the current user. | 4 | 4 | NETWORK |
| CVE‑2019‑8070 | 2019‑09‑12 19:15:12 | CRITICAL (10) | Adobe Flash Player 32.0.0.238 and earlier versions, 32.0.0.207 and earlier versions have a Use after free vulnerability. Successful exploitation could lead to Arbitrary Code Execution in the context of the current user. | 4 | 6 | NETWORK |
| CVE‑2019‑8069 | 2019‑09‑12 19:15:12 | CRITICAL (10) | Adobe Flash Player 32.0.0.238 and earlier versions, 32.0.0.207 and earlier versions have a Same Origin Method Execution vulnerability. Successful exploitation could lead to Arbitrary Code Execution in the context of the current user. | 4 | 6 | NETWORK |
| CVE‑2019‑7845 | 2019‑06‑12 16:29:00 | HIGH (9) | Adobe Flash Player versions 32.0.0.192 and earlier, 32.0.0.192 and earlier, and 32.0.0.192 and earlier have an use after free vulnerability. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2019‑7837 | 2019‑05‑22 19:29:01 | HIGH (9) | Adobe Flash Player versions 32.0.0.171 and earlier, 32.0.0.171 and earlier, and 32.0.0.171 and earlier have a use after free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2019‑7108 | 2019‑05‑23 17:29:01 | HIGH (8) | Adobe Flash Player versions 32.0.0.156 and earlier, 32.0.0.156 and earlier, and 32.0.0.156 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure . | 4 | 4 | NETWORK |
| CVE‑2019‑7096 | 2019‑05‑23 17:29:00 | CRITICAL (10) | Adobe Flash Player versions 32.0.0.156 and earlier, 32.0.0.156 and earlier, and 32.0.0.156 and earlier have an use after free vulnerability. Successful exploitation could lead to arbitrary code execution. | 4 | 6 | NETWORK |
| CVE‑2019‑7090 | 2019‑05‑24 19:29:03 | MEDIUM (4) | Flash Player Desktop Runtime versions 32.0.0.114 and earlier, Flash Player for Google Chrome versions 32.0.0.114 and earlier, and Flash Player for Microsoft Edge and Internet Explorer 11 versions 32.0.0.114 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2019‑13690 | 2023‑08‑25 19:15:08 | CRITICAL (10) | Inappropriate implementation in OS in Google Chrome on ChromeOS prior to 75.0.3770.80 allowed a remote attacker to perform OS-level privilege escalation via a malicious file. (Chromium security severity: High) | 3 | 6 | NETWORK |
| CVE‑2019‑13689 | 2023‑08‑25 19:15:08 | HIGH (8) | Inappropriate implementation in OS in Google Chrome on ChromeOS prior to 75.0.3770.80 allowed a remote attacker to perform arbitrary read/write via a malicious file. (Chromium security severity: Critical) | 2 | 6 | LOCAL |
| CVE‑2019‑0136 | 2019‑06‑13 16:29:01 | LOW (3) | Insufficient access control in the Intel(R) PROSet/Wireless WiFi Software driver before version 21.10 may allow an unauthenticated user to potentially enable denial of service via adjacent access. | 0 | 0 | ADJACENT_NETWORK |
| CVE‑2018‑6151 | 2019‑01‑09 19:29:10 | MEDIUM (7) | Bad cast in DevTools in Google Chrome on Win, Linux, Mac, Chrome OS prior to 66.0.3359.117 allowed an attacker who convinced a user to install a malicious extension to perform an out of bounds memory read via a crafted Chrome Extension. | 0 | 0 | NETWORK |
| CVE‑2018‑5008 | 2018‑07‑20 19:29:03 | MEDIUM (5) | Adobe Flash Player 30.0.0.113 and earlier versions have an Out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑5007 | 2018‑07‑20 19:29:03 | MEDIUM (7) | Adobe Flash Player 30.0.0.113 and earlier versions have a Type Confusion vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 0 | 0 | NETWORK |
| CVE‑2018‑5002 | 2018‑07‑09 19:29:04 | HIGH (10) | Adobe Flash Player versions 29.0.0.171 and earlier have a Stack-based buffer overflow vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 0 | 0 | NETWORK |
| CVE‑2018‑5001 | 2018‑07‑09 19:29:04 | MEDIUM (4) | Adobe Flash Player versions 29.0.0.171 and earlier have an Out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑5000 | 2018‑07‑09 19:29:04 | MEDIUM (4) | Adobe Flash Player versions 29.0.0.171 and earlier have an Integer Overflow vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑4945 | 2018‑07‑09 19:29:00 | MEDIUM (7) | Adobe Flash Player versions 29.0.0.171 and earlier have a Type Confusion vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 0 | 0 | NETWORK |
| CVE‑2018‑4944 | 2018‑05‑19 17:29:02 | HIGH (10) | Adobe Flash Player versions 29.0.0.140 and earlier have an exploitable type confusion vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 0 | 0 | NETWORK |
| CVE‑2018‑4937 | 2018‑05‑19 17:29:01 | HIGH (9) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable out-of-bounds write vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 3 | 6 | NETWORK |
| CVE‑2018‑4936 | 2018‑05‑19 17:29:01 | MEDIUM (7) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable Heap Overflow vulnerability. Successful exploitation could lead to information disclosure. | 3 | 4 | NETWORK |
| CVE‑2018‑4935 | 2018‑05‑19 17:29:01 | HIGH (9) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable out-of-bounds write vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 3 | 6 | NETWORK |
| CVE‑2018‑4934 | 2018‑05‑19 17:29:01 | MEDIUM (7) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 3 | 4 | NETWORK |
| CVE‑2018‑4933 | 2018‑05‑19 17:29:01 | MEDIUM (7) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 3 | 4 | NETWORK |
| CVE‑2018‑4932 | 2018‑05‑19 17:29:01 | HIGH (9) | Adobe Flash Player versions 29.0.0.113 and earlier have an exploitable Use-After-Free vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 3 | 6 | NETWORK |
| CVE‑2018‑4920 | 2018‑05‑19 17:29:01 | HIGH (9) | Adobe Flash Player versions 28.0.0.161 and earlier have an exploitable type confusion vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 3 | 6 | NETWORK |
| CVE‑2018‑4919 | 2018‑05‑19 17:29:01 | HIGH (9) | Adobe Flash Player versions 28.0.0.161 and earlier have an exploitable use after free vulnerability. Successful exploitation could lead to arbitrary code execution in the context of the current user. | 3 | 6 | NETWORK |
| CVE‑2018‑4878 | 2018‑02‑06 21:29:00 | CRITICAL (10) | A use-after-free vulnerability was discovered in Adobe Flash Player before 28.0.0.161. This vulnerability occurs due to a dangling pointer in the Primetime SDK related to media player handling of listener objects. A successful attack can lead to arbitrary code execution. This was exploited in the wild in January and February 2018. | 4 | 6 | NETWORK |
| CVE‑2018‑4877 | 2018‑02‑06 21:29:00 | HIGH (10) | A use-after-free vulnerability was discovered in Adobe Flash Player before 28.0.0.161. This vulnerability occurs due to a dangling pointer in the Primetime SDK related to media player's quality of service functionality. A successful attack can lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2018‑4871 | 2018‑01‑09 21:29:01 | MEDIUM (5) | An Out-of-bounds Read issue was discovered in Adobe Flash Player before 28.0.0.137. This vulnerability occurs because of computation that reads data that is past the end of the target buffer. The use of an invalid (out-of-range) pointer offset during access of internal data structure fields causes the vulnerability. A successful attack can lead to sensitive data exposure. | 0 | 0 | NETWORK |
| CVE‑2018‑15967 | 2018‑09‑25 13:29:02 | MEDIUM (5) | Adobe Flash Player versions 30.0.0.154 and earlier have a privilege escalation vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑12828 | 2018‑08‑29 13:29:01 | HIGH (8) | Adobe Flash Player 30.0.0.134 and earlier have a "use of a component with a known vulnerability" vulnerability. Successful exploitation could lead to privilege escalation. | 0 | 0 | NETWORK |
| CVE‑2018‑12827 | 2018‑08‑29 13:29:01 | MEDIUM (5) | Adobe Flash Player 30.0.0.134 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑12826 | 2018‑08‑29 13:29:01 | MEDIUM (5) | Adobe Flash Player 30.0.0.134 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2018‑12825 | 2018‑08‑29 13:29:01 | HIGH (8) | Adobe Flash Player 30.0.0.134 and earlier have a security bypass vulnerability. Successful exploitation could lead to security mitigation bypass. | 0 | 0 | NETWORK |
| CVE‑2018‑12824 | 2018‑08‑29 13:29:01 | MEDIUM (4) | Adobe Flash Player 30.0.0.134 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | 0 | 0 | NETWORK |
| CVE‑2017‑5084 | 2017‑10‑27 05:29:01 | LOW (2) | Inappropriate implementation in image-burner in Google Chrome OS prior to 59.0.3071.92 allowed a local attacker to read local files via dbus-send commands to a BurnImage D-Bus endpoint. | 0 | 0 | LOCAL |
| CVE‑2017‑3114 | 2017‑12‑09 06:29:03 | HIGH (10) | An issue was discovered in Adobe Flash Player 27.0.0.183 and earlier versions. This vulnerability occurs as a result of a computation that reads data that is past the end of the target buffer; the computation is part of providing language- and region- or country- specific functionality. The use of an invalid (out-of-range) pointer offset during access of internal data structure fields causes the vulnerability. A successful attack can lead to sensitive data exposure. | 0 | 0 | NETWORK |
| CVE‑2017‑3112 | 2017‑12‑09 06:29:03 | HIGH (10) | An issue was discovered in Adobe Flash Player 27.0.0.183 and earlier versions. This vulnerability occurs as a result of a computation that reads data that is past the end of the target buffer; the computation is part of AdobePSDK metadata. The use of an invalid (out-of-range) pointer offset during access of internal data structure fields causes the vulnerability. A successful attack can lead to sensitive data exposure. | 0 | 0 | NETWORK |
| CVE‑2017‑3106 | 2017‑08‑11 19:29:02 | HIGH (9) | Adobe Flash Player versions 26.0.0.137 and earlier have an exploitable type confusion vulnerability when parsing SWF files. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3100 | 2017‑07‑17 13:18:26 | MEDIUM (7) | Adobe Flash Player versions 26.0.0.131 and earlier have an exploitable memory corruption vulnerability in the Action Script 2 BitmapData class. Successful exploitation could lead to memory address disclosure. | 3 | 4 | NETWORK |
| CVE‑2017‑3099 | 2017‑07‑17 13:18:26 | HIGH (9) | Adobe Flash Player versions 26.0.0.131 and earlier have an exploitable memory corruption vulnerability in the Action Script 3 raster data model. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3085 | 2017‑08‑11 19:29:02 | HIGH (7) | Adobe Flash Player versions 26.0.0.137 and earlier have a security bypass vulnerability that leads to information disclosure when performing URL redirect. | 3 | 4 | NETWORK |
| CVE‑2017‑3082 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable memory corruption vulnerability in the LocaleID class. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3081 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable use after free vulnerability during internal computation caused by multiple display object mask manipulations. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3080 | 2017‑07‑17 13:18:26 | MEDIUM (7) | Adobe Flash Player versions 26.0.0.131 and earlier have a security bypass vulnerability related to the Flash API used by Internet Explorer. Successful exploitation could lead to information disclosure. | 3 | 4 | NETWORK |
| CVE‑2017‑3079 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable memory corruption vulnerability in the internal representation of raster data. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3078 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable memory corruption vulnerability in the Adobe Texture Format (ATF) module. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3077 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable memory corruption vulnerability in the PNG image parser. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3076 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable memory corruption vulnerability in the MPEG-4 AVC module. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3075 | 2017‑06‑20 17:29:00 | HIGH (10) | Adobe Flash Player versions 25.0.0.171 and earlier have an exploitable use after free vulnerability when manipulating the ActionsScript 2 XML class. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3074 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable memory corruption vulnerability in the Graphics class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3073 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable use after free vulnerability when handling multiple mask properties of display objects, aka memory corruption. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3072 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable memory corruption vulnerability in the BitmapData class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3071 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable use after free vulnerability when masking display objects. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3070 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable memory corruption vulnerability in the ConvolutionFilter class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3069 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable memory corruption vulnerability in the BlendMode class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3068 | 2017‑05‑09 16:29:00 | HIGH (9) | Adobe Flash Player versions 25.0.0.148 and earlier have an exploitable memory corruption vulnerability in the Advanced Video Coding engine. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3064 | 2017‑04‑12 14:59:03 | HIGH (9) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable memory corruption vulnerability when parsing a shape outline. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3063 | 2017‑04‑12 14:59:03 | HIGH (10) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable use after free vulnerability in the ActionScript2 NetStream class. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3062 | 2017‑04‑12 14:59:03 | HIGH (10) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable use after free vulnerability in ActionScript2 when creating a getter/setter property. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3061 | 2017‑04‑12 14:59:03 | HIGH (10) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable memory corruption vulnerability in the SWF parser. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3060 | 2017‑04‑12 14:59:03 | HIGH (10) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable memory corruption vulnerability in the ActionScript2 code parser. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3059 | 2017‑04‑12 14:59:03 | HIGH (10) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable use after free vulnerability in the internal script object. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3058 | 2017‑04‑12 14:59:03 | HIGH (9) | Adobe Flash Player versions 25.0.0.127 and earlier have an exploitable use after free vulnerability in the sound class. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑3003 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability related to an interaction between the privacy user interface and the ActionScript 2 Camera object. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3002 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability in the ActionScript2 TextField object related to the variable property. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3001 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable use after free vulnerability related to garbage collection in the ActionScript 2 VM. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑3000 | 2017‑03‑14 16:59:00 | MEDIUM (7) | Adobe Flash Player versions 24.0.0.221 and earlier have a vulnerability in the random number generator used for constant blinding. Successful exploitation could lead to information disclosure. | 3 | 4 | NETWORK |
| CVE‑2017‑2999 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable memory corruption vulnerability in the Primetime TVSDK functionality related to hosting playback surface. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2998 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable memory corruption vulnerability in the Primetime TVSDK API functionality related to timeline interactions. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2997 | 2017‑03‑14 16:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.221 and earlier have an exploitable buffer overflow / underflow vulnerability in the Primetime TVSDK that supports customizing ad information. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2996 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable memory corruption vulnerability in Primetime SDK. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2995 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable type confusion vulnerability related to the MessageChannel class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2994 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable use after free vulnerability in Primetime SDK event dispatch. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2993 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable use after free vulnerability related to event handlers. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2992 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable heap overflow vulnerability when parsing an MP4 header. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2991 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable memory corruption vulnerability in the h264 codec (related to decompression). Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2990 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable memory corruption vulnerability in the h264 decompression routine. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2988 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable memory corruption vulnerability when performing garbage collection. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2987 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable integer overflow vulnerability related to Flash Broker COM. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2986 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable heap overflow vulnerability in the Flash Video (FLV) codec. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2985 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable use after free vulnerability in the ActionScript 3 BitmapData class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2984 | 2017‑02‑15 06:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable heap overflow vulnerability in the h264 decoder routine. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2982 | 2017‑02‑15 06:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.194 and earlier have an exploitable use after free vulnerability in a routine related to player shutdown. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2938 | 2017‑01‑11 04:59:01 | MEDIUM (7) | Adobe Flash Player versions 24.0.0.186 and earlier have a security bypass vulnerability related to handling TCP connections. | 3 | 4 | NETWORK |
| CVE‑2017‑2937 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable use after free vulnerability in the ActionScript FileReference class, when using class inheritance. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2936 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable use after free vulnerability in the ActionScript FileReference class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2935 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable heap overflow vulnerability when processing the Flash Video container file format. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2934 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable heap overflow vulnerability when parsing Adobe Texture Format files. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2933 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable heap overflow vulnerability related to texture compression. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2932 | 2017‑01‑11 04:59:01 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable use after free vulnerability in the ActionScript MovieClip class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2931 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable memory corruption vulnerability related to the parsing of SWF metadata. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2930 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable memory corruption vulnerability due to a concurrency error when manipulating a display list. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2928 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable memory corruption vulnerability related to setting visual mode effects. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2927 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable heap overflow vulnerability when processing Adobe Texture Format files. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2926 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable memory corruption vulnerability related to processing of atoms in MP4 files. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑2925 | 2017‑01‑11 04:59:00 | HIGH (9) | Adobe Flash Player versions 24.0.0.186 and earlier have an exploitable memory corruption vulnerability in the JPEG XR codec. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑15403 | 2019‑01‑09 19:29:01 | MEDIUM (4) | Insufficient data validation in crosh could lead to a command injection under chronos privileges in Networking in Google Chrome on Chrome OS prior to 61.0.3163.113 allowed a local attacker to execute arbitrary code via a crafted HTML page. | 0 | 0 | LOCAL |
| CVE‑2017‑15402 | 2019‑01‑09 19:29:00 | MEDIUM (7) | Using an ID that can be controlled by a compromised renderer which allows any frame to overwrite the page_state of any other frame in the same process in Navigation in Google Chrome on Chrome OS prior to 62.0.3202.74 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. | 0 | 0 | NETWORK |
| CVE‑2017‑15400 | 2018‑02‑07 23:29:01 | HIGH (9) | Insufficient restriction of IPP filters in CUPS in Google Chrome OS prior to 62.0.3202.74 allowed a remote attacker to execute a command with the same privileges as the cups daemon via a crafted PPD file, aka a printer zeroconfig CRLF issue. | 0 | 0 | NETWORK |
| CVE‑2017‑15397 | 2018‑02‑07 23:29:01 | MEDIUM (6) | Inappropriate implementation in ChromeVox in Google Chrome OS prior to 62.0.3202.74 allowed a remote attacker in a privileged network position to observe or tamper with certain cleartext HTTP requests by leveraging that position. | 0 | 0 | NETWORK |
| CVE‑2017‑11305 | 2017‑12‑13 21:29:00 | MEDIUM (7) | A regression affecting Adobe Flash Player version 27.0.0.187 (and earlier versions) causes the unintended reset of the global settings preference file when a user clears browser data. | 3 | 4 | NETWORK |
| CVE‑2017‑11292 | 2017‑10‑22 19:29:00 | HIGH (9) | Adobe Flash Player version 27.0.0.159 and earlier has a flawed bytecode verification procedure, which allows for an untrusted value to be used in the calculation of an array index. This can lead to type confusion, and successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2017‑11282 | 2017‑12‑01 08:29:00 | HIGH (8) | Adobe Flash Player has an exploitable memory corruption vulnerability in the MP4 atom parser. Successful exploitation could lead to arbitrary code execution. This affects 26.0.0.151 and earlier. | 0 | 0 | NETWORK |
| CVE‑2017‑11281 | 2017‑12‑01 08:29:00 | HIGH (8) | Adobe Flash Player has an exploitable memory corruption vulnerability in the text handling function. Successful exploitation could lead to arbitrary code execution. This affects 26.0.0.151 and earlier. | 0 | 0 | NETWORK |
| CVE‑2017‑11225 | 2017‑12‑09 06:29:00 | HIGH (10) | An issue was discovered in Adobe Flash Player 27.0.0.183 and earlier versions. This vulnerability is an instance of a use after free vulnerability in the Primetime SDK metadata functionality. The mismatch between an old and a new object can provide an attacker with unintended memory access -- potentially leading to code corruption, control-flow hijack, or an information leak attack. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑11215 | 2017‑12‑09 06:29:00 | HIGH (10) | An issue was discovered in Adobe Flash Player 27.0.0.183 and earlier versions. This vulnerability is an instance of a use after free vulnerability in the Primetime SDK. The mismatch between an old and a new object can provide an attacker with unintended memory access -- potentially leading to code corruption, control-flow hijack, or an information leak attack. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2017‑11213 | 2017‑12‑09 06:29:00 | HIGH (10) | An issue was discovered in Adobe Flash Player 27.0.0.183 and earlier versions. This vulnerability occurs as a result of a computation that reads data that is past the end of the target buffer due to an integer overflow; the computation is part of the abstraction that creates an arbitrarily sized transparent or opaque bitmap image. The use of an invalid (out-of-range) pointer offset during access of internal data structure fields causes the vulnerability. A successful attack can lead to sensitive data exposure. | 0 | 0 | NETWORK |
| CVE‑2016‑7892 | 2016‑12‑15 06:59:56 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the TextField class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7890 | 2016‑12‑15 06:59:54 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have security bypass vulnerability in the implementation of the same origin policy. | 3 | 6 | NETWORK |
| CVE‑2016‑7881 | 2016‑12‑15 06:59:45 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the MovieClip class when handling conversion to an object. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7880 | 2016‑12‑15 06:59:44 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability when setting the length property of an array object. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7879 | 2016‑12‑15 06:59:43 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the NetConnection class when handling an attached script object. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7878 | 2016‑12‑15 06:59:42 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the PSDK's MediaPlayer class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7877 | 2016‑12‑15 06:59:41 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the Action Message Format serialization (AFM0). Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7876 | 2016‑12‑15 06:59:40 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable memory corruption vulnerability in the Clipboard class related to data handling functionality. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7875 | 2016‑12‑15 06:59:39 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable integer overflow vulnerability in the BitmapData class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7874 | 2016‑12‑15 06:59:38 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable memory corruption vulnerability in the NetConnection class when handling the proxy types. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7873 | 2016‑12‑15 06:59:37 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable memory corruption vulnerability in the PSDK class related to ad policy functionality method. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7872 | 2016‑12‑15 06:59:36 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable use after free vulnerability in the MovieClip class related to objects at multiple presentation levels. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7871 | 2016‑12‑15 06:59:35 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable memory corruption vulnerability in the Worker class. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7870 | 2016‑12‑15 06:59:34 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable buffer overflow / underflow vulnerability in the RegExp class for specific search strategies. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7869 | 2016‑12‑15 06:59:33 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable buffer overflow / underflow vulnerability in the RegExp class related to backtrack search functionality. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7868 | 2016‑12‑15 06:59:32 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable buffer overflow / underflow vulnerability in the RegExp class related to alternation functionality. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7867 | 2016‑12‑15 06:59:31 | HIGH (9) | Adobe Flash Player versions 23.0.0.207 and earlier, 11.2.202.644 and earlier have an exploitable buffer overflow / underflow vulnerability in the RegExp class related to bookmarking in searches. Successful exploitation could lead to arbitrary code execution. | 3 | 6 | NETWORK |
| CVE‑2016‑7865 | 2016‑11‑08 17:59:10 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable type confusion vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7864 | 2016‑11‑08 17:59:09 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7863 | 2016‑11‑08 17:59:08 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7862 | 2016‑11‑08 17:59:07 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7861 | 2016‑11‑08 17:59:06 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable type confusion vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7860 | 2016‑11‑08 17:59:05 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable type confusion vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7859 | 2016‑11‑08 17:59:03 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7858 | 2016‑11‑08 17:59:02 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7857 | 2016‑11‑08 17:59:01 | HIGH (9) | Adobe Flash Player versions 23.0.0.205 and earlier, 11.2.202.643 and earlier have an exploitable use-after-free vulnerability. Successful exploitation could lead to arbitrary code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑7855 | 2016‑11‑01 22:59:00 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 23.0.0.205 on Windows and OS X and before 11.2.202.643 on Linux allows remote attackers to execute arbitrary code via unspecified vectors, as exploited in the wild in October 2016. | 0 | 0 | NETWORK |
| CVE‑2016‑7020 | 2016‑10‑05 21:59:01 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑6992 | 2016‑10‑13 20:00:09 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code by leveraging an unspecified "type confusion." | 3 | 6 | NETWORK |
| CVE‑2016‑6990 | 2016‑10‑13 20:00:06 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6983, CVE-2016-6984, CVE-2016-6985, CVE-2016-6986, and CVE-2016-6989. | 3 | 6 | NETWORK |
| CVE‑2016‑6989 | 2016‑10‑13 20:00:03 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6983, CVE-2016-6984, CVE-2016-6985, CVE-2016-6986, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6987 | 2016‑10‑13 20:00:00 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-6981. | 3 | 6 | NETWORK |
| CVE‑2016‑6986 | 2016‑10‑13 19:59:58 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6983, CVE-2016-6984, CVE-2016-6985, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6985 | 2016‑10‑13 19:59:57 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6983, CVE-2016-6984, CVE-2016-6986, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6984 | 2016‑10‑13 19:59:56 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6983, CVE-2016-6985, CVE-2016-6986, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6983 | 2016‑10‑13 19:59:55 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6982, CVE-2016-6984, CVE-2016-6985, CVE-2016-6986, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6982 | 2016‑10‑13 19:59:54 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4273, CVE-2016-6983, CVE-2016-6984, CVE-2016-6985, CVE-2016-6986, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑6981 | 2016‑10‑13 19:59:53 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-6987. | 3 | 6 | NETWORK |
| CVE‑2016‑6932 | 2016‑09‑14 18:59:28 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, and CVE-2016-6931. | 3 | 6 | NETWORK |
| CVE‑2016‑6931 | 2016‑09‑14 18:59:27 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6930 | 2016‑09‑14 18:59:26 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6929 | 2016‑09‑14 18:59:25 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6927 | 2016‑09‑14 18:59:24 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6926 | 2016‑09‑14 18:59:23 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6925 | 2016‑09‑14 18:59:22 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6924 | 2016‑09‑14 18:59:21 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, and CVE-2016-6922. | 3 | 6 | NETWORK |
| CVE‑2016‑6923 | 2016‑09‑14 18:59:20 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6921, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑6922 | 2016‑09‑14 18:59:19 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑6921 | 2016‑09‑14 18:59:18 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-4279, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑5169 | 2016‑09‑25 20:59:00 | MEDIUM (7) | Format string vulnerability in Google Chrome OS before 53.0.2785.103 allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2016‑4287 | 2016‑09‑14 18:59:17 | HIGH (9) | Integer overflow in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors. | 3 | 6 | NETWORK |
| CVE‑2016‑4286 | 2016‑10‑13 19:59:05 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to bypass intended access restrictions via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2016‑4285 | 2016‑09‑14 18:59:16 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4284 | 2016‑09‑14 18:59:15 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4283 | 2016‑09‑14 18:59:14 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4282 | 2016‑09‑14 18:59:12 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4281 | 2016‑09‑14 18:59:11 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4280 | 2016‑09‑14 18:59:10 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4276, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4279 | 2016‑09‑14 18:59:09 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4272, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑4278 | 2016‑09‑14 18:59:08 | MEDIUM (7) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to bypass intended access restrictions and obtain sensitive information via unspecified vectors, a different vulnerability than CVE-2016-4271 and CVE-2016-4277. | 3 | 4 | NETWORK |
| CVE‑2016‑4277 | 2016‑09‑14 18:59:07 | MEDIUM (7) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to bypass intended access restrictions and obtain sensitive information via unspecified vectors, a different vulnerability than CVE-2016-4271 and CVE-2016-4278. | 3 | 4 | NETWORK |
| CVE‑2016‑4276 | 2016‑09‑14 18:59:05 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4275, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4275 | 2016‑09‑14 18:59:04 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4274, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4274 | 2016‑09‑14 18:59:03 | HIGH (9) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4275, CVE-2016-4276, CVE-2016-4280, CVE-2016-4281, CVE-2016-4282, CVE-2016-4283, CVE-2016-4284, CVE-2016-4285, CVE-2016-6922, and CVE-2016-6924. | 3 | 6 | NETWORK |
| CVE‑2016‑4273 | 2016‑10‑13 19:59:04 | HIGH (9) | Adobe Flash Player before 18.0.0.382 and 19.x through 23.x before 23.0.0.185 on Windows and OS X and before 11.2.202.637 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-6982, CVE-2016-6983, CVE-2016-6984, CVE-2016-6985, CVE-2016-6986, CVE-2016-6989, and CVE-2016-6990. | 3 | 6 | NETWORK |
| CVE‑2016‑4272 | 2016‑09‑14 18:59:02 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4279, CVE-2016-6921, CVE-2016-6923, CVE-2016-6925, CVE-2016-6926, CVE-2016-6927, CVE-2016-6929, CVE-2016-6930, CVE-2016-6931, and CVE-2016-6932. | 3 | 6 | NETWORK |
| CVE‑2016‑4271 | 2016‑09‑14 18:59:00 | MEDIUM (7) | Adobe Flash Player before 18.0.0.375 and 19.x through 23.x before 23.0.0.162 on Windows and OS X and before 11.2.202.635 on Linux allows attackers to bypass intended access restrictions and obtain sensitive information via unspecified vectors, a different vulnerability than CVE-2016-4277 and CVE-2016-4278, aka a "local-with-filesystem Flash sandbox bypass" issue. | 3 | 4 | NETWORK |
| CVE‑2016‑4249 | 2016‑07‑13 02:00:56 | HIGH (9) | Heap-based buffer overflow in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors. | 3 | 6 | NETWORK |
| CVE‑2016‑4248 | 2016‑07‑13 02:00:55 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, and CVE-2016-4231. | 3 | 6 | NETWORK |
| CVE‑2016‑4247 | 2016‑07‑13 02:00:54 | MEDIUM (5) | Race condition in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to obtain sensitive information via unspecified vectors. | 2 | 4 | NETWORK |
| CVE‑2016‑4246 | 2016‑07‑13 02:00:52 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, and CVE-2016-4245. | 3 | 6 | NETWORK |
| CVE‑2016‑4245 | 2016‑07‑13 02:00:51 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4244 | 2016‑07‑13 02:00:51 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4243 | 2016‑07‑13 02:00:50 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4242 | 2016‑07‑13 02:00:49 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4241 | 2016‑07‑13 02:00:48 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4240 | 2016‑07‑13 02:00:47 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4239 | 2016‑07‑13 02:00:46 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4238 | 2016‑07‑13 02:00:45 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4237 | 2016‑07‑13 02:00:44 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4236 | 2016‑07‑13 02:00:43 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4235 | 2016‑07‑13 02:00:42 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4234 | 2016‑07‑13 02:00:42 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4233 | 2016‑07‑13 02:00:41 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4232 | 2016‑07‑13 02:00:40 | HIGH (8) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to obtain sensitive information from process memory via unspecified vectors. | 4 | 4 | NETWORK |
| CVE‑2016‑4231 | 2016‑07‑13 02:00:39 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4230 | 2016‑07‑13 02:00:38 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4229 | 2016‑07‑13 02:00:37 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4228 | 2016‑07‑13 02:00:36 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4227 | 2016‑07‑13 02:00:35 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4226 | 2016‑07‑13 02:00:34 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4222, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4225 | 2016‑07‑13 02:00:33 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code by leveraging an unspecified "type confusion," a different vulnerability than CVE-2016-4223 and CVE-2016-4224. | 3 | 6 | NETWORK |
| CVE‑2016‑4224 | 2016‑07‑13 02:00:32 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code by leveraging an unspecified "type confusion," a different vulnerability than CVE-2016-4223 and CVE-2016-4225. | 3 | 6 | NETWORK |
| CVE‑2016‑4223 | 2016‑07‑13 02:00:31 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code by leveraging an unspecified "type confusion," a different vulnerability than CVE-2016-4224 and CVE-2016-4225. | 3 | 6 | NETWORK |
| CVE‑2016‑4222 | 2016‑07‑13 02:00:30 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4174, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4221 | 2016‑07‑13 02:00:29 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4220 | 2016‑07‑13 02:00:29 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4219 | 2016‑07‑13 02:00:28 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4218 | 2016‑07‑13 02:00:27 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4217 | 2016‑07‑13 02:00:26 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4190 | 2016‑07‑13 02:00:00 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4189 | 2016‑07‑13 01:59:59 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4188 | 2016‑07‑13 01:59:58 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4187 | 2016‑07‑13 01:59:57 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4186 | 2016‑07‑13 01:59:56 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4185 | 2016‑07‑13 01:59:55 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4184 | 2016‑07‑13 01:59:54 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4183 | 2016‑07‑13 01:59:53 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4182 | 2016‑07‑13 01:59:52 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4181 | 2016‑07‑13 01:59:51 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4180 | 2016‑07‑13 01:59:50 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4179, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4179 | 2016‑07‑13 01:59:49 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4175, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4178 | 2016‑07‑13 01:59:48 | MEDIUM (4) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to bypass intended access restrictions and obtain sensitive information via unspecified vectors. | 3 | 1 | NETWORK |
| CVE‑2016‑4177 | 2016‑07‑13 01:59:47 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (stack memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4176. | 3 | 6 | NETWORK |
| CVE‑2016‑4176 | 2016‑07‑13 01:59:46 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (stack memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4177. | 3 | 6 | NETWORK |
| CVE‑2016‑4175 | 2016‑07‑13 01:59:45 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4172, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4174 | 2016‑07‑13 01:59:44 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4173, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4173 | 2016‑07‑13 01:59:43 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-4174, CVE-2016-4222, CVE-2016-4226, CVE-2016-4227, CVE-2016-4228, CVE-2016-4229, CVE-2016-4230, CVE-2016-4231, and CVE-2016-4248. | 3 | 6 | NETWORK |
| CVE‑2016‑4172 | 2016‑07‑13 01:59:42 | HIGH (9) | Adobe Flash Player before 18.0.0.366 and 19.x through 22.x before 22.0.0.209 on Windows and OS X and before 11.2.202.632 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-4175, CVE-2016-4179, CVE-2016-4180, CVE-2016-4181, CVE-2016-4182, CVE-2016-4183, CVE-2016-4184, CVE-2016-4185, CVE-2016-4186, CVE-2016-4187, CVE-2016-4188, CVE-2016-4189, CVE-2016-4190, CVE-2016-4217, CVE-2016-4218, CVE-2016-4219, CVE-2016-4220, CVE-2016-4221, CVE-2016-4233, CVE-2016-4234, CVE-2016-4235, CVE-2016-4236, CVE-2016-4237, CVE-2016-4238, CVE-2016-4239, CVE-2016-4240, CVE-2016-4241, CVE-2016-4242, CVE-2016-4243, CVE-2016-4244, CVE-2016-4245, and CVE-2016-4246. | 3 | 6 | NETWORK |
| CVE‑2016‑4171 | 2016‑06‑16 14:59:51 | CRITICAL (10) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier allows remote attackers to execute arbitrary code via unknown vectors, as exploited in the wild in June 2016. | 4 | 6 | NETWORK |
| CVE‑2016‑4166 | 2016‑06‑16 14:59:49 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4163 | 2016‑06‑16 14:59:46 | CRITICAL (10) | Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1096, CVE-2016-1098, CVE-2016-1099, CVE-2016-1100, CVE-2016-1102, CVE-2016-1104, CVE-2016-4109, CVE-2016-4111, CVE-2016-4112, CVE-2016-4113, CVE-2016-4114, CVE-2016-4115, CVE-2016-4120, CVE-2016-4160, CVE-2016-4161, and CVE-2016-4162. | 4 | 6 | NETWORK |
| CVE‑2016‑4162 | 2016‑06‑16 14:59:45 | CRITICAL (10) | Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1096, CVE-2016-1098, CVE-2016-1099, CVE-2016-1100, CVE-2016-1102, CVE-2016-1104, CVE-2016-4109, CVE-2016-4111, CVE-2016-4112, CVE-2016-4113, CVE-2016-4114, CVE-2016-4115, CVE-2016-4120, CVE-2016-4160, CVE-2016-4161, and CVE-2016-4163. | 4 | 6 | NETWORK |
| CVE‑2016‑4161 | 2016‑06‑16 14:59:44 | CRITICAL (10) | Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1096, CVE-2016-1098, CVE-2016-1099, CVE-2016-1100, CVE-2016-1102, CVE-2016-1104, CVE-2016-4109, CVE-2016-4111, CVE-2016-4112, CVE-2016-4113, CVE-2016-4114, CVE-2016-4115, CVE-2016-4120, CVE-2016-4160, CVE-2016-4162, and CVE-2016-4163. | 4 | 6 | NETWORK |
| CVE‑2016‑4160 | 2016‑06‑16 14:59:43 | CRITICAL (10) | Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1096, CVE-2016-1098, CVE-2016-1099, CVE-2016-1100, CVE-2016-1102, CVE-2016-1104, CVE-2016-4109, CVE-2016-4111, CVE-2016-4112, CVE-2016-4113, CVE-2016-4114, CVE-2016-4115, CVE-2016-4120, CVE-2016-4161, CVE-2016-4162, and CVE-2016-4163. | 4 | 6 | NETWORK |
| CVE‑2016‑4156 | 2016‑06‑16 14:59:38 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4155 | 2016‑06‑16 14:59:38 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4154 | 2016‑06‑16 14:59:37 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4153 | 2016‑06‑16 14:59:36 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4152 | 2016‑06‑16 14:59:34 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4151 | 2016‑06‑16 14:59:33 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4150 | 2016‑06‑16 14:59:32 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4149 | 2016‑06‑16 14:59:31 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4148 | 2016‑06‑16 14:59:30 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4147 | 2016‑06‑16 14:59:29 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4146 | 2016‑06‑16 14:59:28 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4145 | 2016‑06‑16 14:59:27 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4144 | 2016‑06‑16 14:59:26 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4143 | 2016‑06‑16 14:59:25 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4142 | 2016‑06‑16 14:59:24 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4141 | 2016‑06‑16 14:59:23 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4140 | 2016‑06‑16 14:59:22 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4139 | 2016‑06‑16 14:59:21 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4138 | 2016‑06‑16 14:59:19 | CRITICAL (10) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 4 | 6 | NETWORK |
| CVE‑2016‑4137 | 2016‑06‑16 14:59:18 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4136 | 2016‑06‑16 14:59:18 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4135 | 2016‑06‑16 14:59:17 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4134 | 2016‑06‑16 14:59:16 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4133 | 2016‑06‑16 14:59:14 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4132 | 2016‑06‑16 14:59:13 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4131 | 2016‑06‑16 14:59:12 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4130 | 2016‑06‑16 14:59:11 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4129 | 2016‑06‑16 14:59:10 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4128 | 2016‑06‑16 14:59:09 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4127 | 2016‑06‑16 14:59:08 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4125 | 2016‑06‑16 14:59:06 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4124 | 2016‑06‑16 14:59:05 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4123 | 2016‑06‑16 14:59:04 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4122 | 2016‑06‑16 14:59:03 | HIGH (9) | Unspecified vulnerability in Adobe Flash Player 21.0.0.242 and earlier, as used in the Adobe Flash libraries in Microsoft Internet Explorer 10 and 11 and Microsoft Edge, has unknown impact and attack vectors, a different vulnerability than other CVEs listed in MS16-083. | 3 | 6 | NETWORK |
| CVE‑2016‑4121 | 2016‑06‑16 14:59:02 | CRITICAL (10) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-1097, CVE-2016-1106, CVE-2016-1107, CVE-2016-1108, CVE-2016-1109, CVE-2016-1110, CVE-2016-4108, and CVE-2016-4110. | 4 | 6 | NETWORK |
| CVE‑2016‑4120 | 2016‑06‑16 14:59:00 | CRITICAL (10) | Adobe Flash Player before 18.0.0.352 and 19.x through 21.x before 21.0.0.242 on Windows and OS X and before 11.2.202.621 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1096, CVE-2016-1098, CVE-2016-1099, CVE-2016-1100, CVE-2016-1102, CVE-2016-1104, CVE-2016-4109, CVE-2016-4111, CVE-2016-4112, CVE-2016-4113, CVE-2016-4114, CVE-2016-4115, CVE-2016-4160, CVE-2016-4161, CVE-2016-4162, and CVE-2016-4163. | 4 | 6 | NETWORK |
| CVE‑2016‑1033 | 2016‑04‑09 01:59:48 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, and CVE-2016-1032. | 3 | 6 | NETWORK |
| CVE‑2016‑1032 | 2016‑04‑09 01:59:47 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1031 | 2016‑04‑09 01:59:46 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-1011, CVE-2016-1013, CVE-2016-1016, and CVE-2016-1017. | 3 | 6 | NETWORK |
| CVE‑2016‑1030 | 2016‑04‑09 01:59:45 | HIGH (8) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to bypass intended access restrictions via unspecified vectors. | 3 | 5 | NETWORK |
| CVE‑2016‑1029 | 2016‑04‑09 01:59:44 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1028 | 2016‑04‑09 01:59:43 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1027 | 2016‑04‑09 01:59:42 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1026 | 2016‑04‑09 01:59:41 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1025 | 2016‑04‑09 01:59:40 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1024 | 2016‑04‑09 01:59:39 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1023 | 2016‑04‑09 01:59:38 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1022 | 2016‑04‑09 01:59:37 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1021, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1021 | 2016‑04‑09 01:59:36 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1020, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1020 | 2016‑04‑09 01:59:35 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1012, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1019 | 2016‑04‑07 10:59:01 | CRITICAL (10) | Adobe Flash Player 21.0.0.197 and earlier allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via unspecified vectors, as exploited in the wild in April 2016. | 4 | 6 | NETWORK |
| CVE‑2016‑1018 | 2016‑04‑09 01:59:34 | HIGH (9) | Stack-based buffer overflow in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via crafted JPEG-XR data. | 3 | 6 | NETWORK |
| CVE‑2016‑1017 | 2016‑04‑09 01:59:33 | HIGH (9) | Use-after-free vulnerability in the LoadVars.decode function in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-1011, CVE-2016-1013, CVE-2016-1016, and CVE-2016-1031. | 3 | 6 | NETWORK |
| CVE‑2016‑1016 | 2016‑04‑09 01:59:32 | HIGH (9) | Use-after-free vulnerability in the Transform object implementation in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via a flash.geom.Matrix callback, a different vulnerability than CVE-2016-1011, CVE-2016-1013, CVE-2016-1017, and CVE-2016-1031. | 3 | 6 | NETWORK |
| CVE‑2016‑1015 | 2016‑04‑09 01:59:31 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code by overriding NetConnection object properties to leverage an unspecified "type confusion," a different vulnerability than CVE-2016-1019. | 3 | 6 | NETWORK |
| CVE‑2016‑1014 | 2016‑04‑09 01:59:30 | HIGH (7) | Untrusted search path vulnerability in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows local users to gain privileges via a Trojan horse resource in an unspecified directory. | 1 | 6 | LOCAL |
| CVE‑2016‑1013 | 2016‑04‑09 01:59:29 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-1011, CVE-2016-1016, CVE-2016-1017, and CVE-2016-1031. | 3 | 6 | NETWORK |
| CVE‑2016‑1012 | 2016‑04‑09 01:59:28 | HIGH (9) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-1020, CVE-2016-1021, CVE-2016-1022, CVE-2016-1023, CVE-2016-1024, CVE-2016-1025, CVE-2016-1026, CVE-2016-1027, CVE-2016-1028, CVE-2016-1029, CVE-2016-1032, and CVE-2016-1033. | 3 | 6 | NETWORK |
| CVE‑2016‑1011 | 2016‑04‑09 01:59:27 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-1013, CVE-2016-1016, CVE-2016-1017, and CVE-2016-1031. | 3 | 6 | NETWORK |
| CVE‑2016‑1010 | 2016‑03‑12 15:59:25 | HIGH (9) | Integer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0963 and CVE-2016-0993. | 3 | 6 | NETWORK |
| CVE‑2016‑1006 | 2016‑04‑09 01:59:26 | HIGH (8) | Adobe Flash Player before 18.0.0.343 and 19.x through 21.x before 21.0.0.213 on Windows and OS X and before 11.2.202.616 on Linux allows attackers to bypass the ASLR protection mechanism via JIT data. | 3 | 5 | NETWORK |
| CVE‑2016‑1005 | 2016‑03‑12 15:59:24 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (uninitialized pointer dereference and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, and CVE-2016-1002. | 3 | 6 | NETWORK |
| CVE‑2016‑1002 | 2016‑03‑12 15:59:23 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑1001 | 2016‑03‑12 15:59:22 | HIGH (9) | Heap-based buffer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors. | 3 | 6 | NETWORK |
| CVE‑2016‑1000 | 2016‑03‑12 15:59:21 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, and CVE-2016-0999. | 3 | 6 | NETWORK |
| CVE‑2016‑0999 | 2016‑03‑12 15:59:20 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0998 | 2016‑03‑12 15:59:19 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0997 | 2016‑03‑12 15:59:18 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0996 | 2016‑03‑12 15:59:17 | HIGH (9) | Use-after-free vulnerability in the setInterval method in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via crafted arguments, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0995 | 2016‑03‑12 15:59:16 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0994 | 2016‑03‑12 15:59:15 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code by using the actionCallMethod opcode with crafted arguments, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0993 | 2016‑03‑12 15:59:14 | HIGH (9) | Integer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0963 and CVE-2016-1010. | 3 | 6 | NETWORK |
| CVE‑2016‑0992 | 2016‑03‑12 15:59:13 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0991 | 2016‑03‑12 15:59:12 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0990, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0990 | 2016‑03‑12 15:59:11 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0988, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0989 | 2016‑03‑12 15:59:10 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0992, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0988 | 2016‑03‑12 15:59:09 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0987, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0987 | 2016‑03‑12 15:59:08 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0988, CVE-2016-0990, CVE-2016-0991, CVE-2016-0994, CVE-2016-0995, CVE-2016-0996, CVE-2016-0997, CVE-2016-0998, CVE-2016-0999, and CVE-2016-1000. | 3 | 6 | NETWORK |
| CVE‑2016‑0986 | 2016‑03‑12 15:59:07 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0962, CVE-2016-0989, CVE-2016-0992, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0985 | 2016‑02‑10 20:59:34 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code by leveraging an unspecified "type confusion." | 3 | 6 | NETWORK |
| CVE‑2016‑0984 | 2016‑02‑10 20:59:33 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0973, CVE-2016-0974, CVE-2016-0975, CVE-2016-0982, and CVE-2016-0983. | 3 | 6 | NETWORK |
| CVE‑2016‑0983 | 2016‑02‑10 20:59:32 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0973, CVE-2016-0974, CVE-2016-0975, CVE-2016-0982, and CVE-2016-0984. | 3 | 6 | NETWORK |
| CVE‑2016‑0982 | 2016‑02‑10 20:59:31 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0973, CVE-2016-0974, CVE-2016-0975, CVE-2016-0983, and CVE-2016-0984. | 3 | 6 | NETWORK |
| CVE‑2016‑0981 | 2016‑02‑10 20:59:30 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, and CVE-2016-0980. | 3 | 6 | NETWORK |
| CVE‑2016‑0980 | 2016‑02‑10 20:59:28 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0979 | 2016‑02‑10 20:59:27 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0978 | 2016‑02‑10 20:59:26 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0977 | 2016‑02‑10 20:59:25 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0976 | 2016‑02‑10 20:59:24 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0975 | 2016‑02‑10 20:59:23 | HIGH (9) | Use-after-free vulnerability in the instanceof function in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code by leveraging improper reference handling, a different vulnerability than CVE-2016-0973, CVE-2016-0974, CVE-2016-0982, CVE-2016-0983, and CVE-2016-0984. | 3 | 6 | NETWORK |
| CVE‑2016‑0974 | 2016‑02‑10 20:59:22 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0973, CVE-2016-0975, CVE-2016-0982, CVE-2016-0983, and CVE-2016-0984. | 3 | 6 | NETWORK |
| CVE‑2016‑0973 | 2016‑02‑10 20:59:21 | HIGH (9) | Use-after-free vulnerability in the URLRequest object implementation in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via a URLLoader.load call, a different vulnerability than CVE-2016-0974, CVE-2016-0975, CVE-2016-0982, CVE-2016-0983, and CVE-2016-0984. | 3 | 6 | NETWORK |
| CVE‑2016‑0972 | 2016‑02‑10 20:59:20 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0971 | 2016‑02‑10 20:59:19 | HIGH (9) | Heap-based buffer overflow in Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allows attackers to execute arbitrary code via unspecified vectors. | 3 | 6 | NETWORK |
| CVE‑2016‑0970 | 2016‑02‑10 20:59:18 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0969 | 2016‑02‑10 20:59:17 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0968 | 2016‑02‑10 20:59:16 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0967 | 2016‑02‑10 20:59:15 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0966, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0966 | 2016‑02‑10 20:59:14 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0965, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0965 | 2016‑02‑10 20:59:13 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0964, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0964 | 2016‑02‑10 20:59:12 | HIGH (9) | Adobe Flash Player before 18.0.0.329 and 19.x and 20.x before 20.0.0.306 on Windows and OS X and before 11.2.202.569 on Linux, Adobe AIR before 20.0.0.260, Adobe AIR SDK before 20.0.0.260, and Adobe AIR SDK & Compiler before 20.0.0.260 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0965, CVE-2016-0966, CVE-2016-0967, CVE-2016-0968, CVE-2016-0969, CVE-2016-0970, CVE-2016-0972, CVE-2016-0976, CVE-2016-0977, CVE-2016-0978, CVE-2016-0979, CVE-2016-0980, and CVE-2016-0981. | 3 | 6 | NETWORK |
| CVE‑2016‑0963 | 2016‑03‑12 15:59:06 | HIGH (9) | Integer overflow in Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allows attackers to execute arbitrary code via unspecified vectors, a different vulnerability than CVE-2016-0993 and CVE-2016-1010. | 3 | 6 | NETWORK |
| CVE‑2016‑0962 | 2016‑03‑12 15:59:05 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0961, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0961 | 2016‑03‑12 15:59:04 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0960, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0960 | 2016‑03‑12 15:59:03 | HIGH (9) | Adobe Flash Player before 18.0.0.333 and 19.x through 21.x before 21.0.0.182 on Windows and OS X and before 11.2.202.577 on Linux, Adobe AIR before 21.0.0.176, Adobe AIR SDK before 21.0.0.176, and Adobe AIR SDK & Compiler before 21.0.0.176 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2016-0961, CVE-2016-0962, CVE-2016-0986, CVE-2016-0989, CVE-2016-0992, CVE-2016-1002, and CVE-2016-1005. | 3 | 6 | NETWORK |
| CVE‑2016‑0959 | 2017‑06‑27 20:29:01 | HIGH (10) | Use after free vulnerability in Adobe Flash Player Desktop Runtime before 20.0.0.267, Adobe Flash Player Extended Support Release before 18.0.0.324, Adobe Flash Player for Google Chrome before 20.0.0.267, Adobe Flash Player for Microsoft Edge and Internet Explorer 11 before 20.0.0.267, Adobe Flash Player for Internet Explorer 10 and 11 before 20.0.0.267, Adobe Flash Player for Linux before 11.2.202.559, AIR Desktop Runtime before 20.0.0.233, AIR SDK before 20.0.0.233, AIR SDK & Compiler before 20.0.0.233, AIR for Android before 20.0.0.233. | 0 | 0 | NETWORK |
| CVE‑2015‑8823 | 2016‑04‑22 18:59:00 | HIGH (9) | Use-after-free vulnerability in the TextField object implementation in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via crafted text property, a different vulnerability than CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8452, CVE-2015-8454, CVE-2015-8653, CVE-2015-8655, CVE-2015-8821, and CVE-2015-8822. | 3 | 6 | NETWORK |
| CVE‑2015‑8822 | 2016‑03‑04 23:59:11 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via crafted MPEG-4 data, a different vulnerability than CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8452, CVE-2015-8454, CVE-2015-8653, CVE-2015-8655, and CVE-2015-8821. | 3 | 6 | NETWORK |
| CVE‑2015‑8821 | 2016‑03‑04 23:59:10 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via crafted MPEG-4 data, a different vulnerability than CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8452, CVE-2015-8454, CVE-2015-8653, CVE-2015-8655, and CVE-2015-8822. | 3 | 6 | NETWORK |
| CVE‑2015‑8820 | 2016‑03‑04 23:59:09 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (out-of-bounds read and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8652, CVE-2015-8654, CVE-2015-8656, CVE-2015-8657, and CVE-2015-8658. | 3 | 6 | NETWORK |
| CVE‑2015‑8658 | 2016‑03‑04 23:59:08 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (uninitialized pointer dereference and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8652, CVE-2015-8654, CVE-2015-8656, CVE-2015-8657, and CVE-2015-8820. | 3 | 6 | NETWORK |
| CVE‑2015‑8657 | 2016‑03‑04 23:59:07 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (out-of-bounds read and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8652, CVE-2015-8654, CVE-2015-8656, CVE-2015-8658, and CVE-2015-8820. | 3 | 6 | NETWORK |
| CVE‑2015‑8656 | 2016‑03‑04 23:59:05 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (out-of-bounds read and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8652, CVE-2015-8654, CVE-2015-8657, CVE-2015-8658, and CVE-2015-8820. | 3 | 6 | NETWORK |
| CVE‑2015‑8655 | 2016‑03‑04 23:59:04 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via crafted MPEG-4 data, a different vulnerability than CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8452, CVE-2015-8454, CVE-2015-8653, CVE-2015-8821, and CVE-2015-8822. | 3 | 6 | NETWORK |
| CVE‑2015‑8654 | 2016‑03‑04 23:59:03 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (out-of-bounds read and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8652, CVE-2015-8656, CVE-2015-8657, CVE-2015-8658, and CVE-2015-8820. | 3 | 6 | NETWORK |
| CVE‑2015‑8653 | 2016‑03‑04 23:59:02 | HIGH (9) | Use-after-free vulnerability in Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allows attackers to execute arbitrary code via crafted MPEG-4 data, a different vulnerability than CVE-2015-8048, CVE-2015-8049, CVE-2015-8050, CVE-2015-8055, CVE-2015-8056, CVE-2015-8057, CVE-2015-8058, CVE-2015-8059, CVE-2015-8061, CVE-2015-8062, CVE-2015-8063, CVE-2015-8064, CVE-2015-8065, CVE-2015-8066, CVE-2015-8067, CVE-2015-8068, CVE-2015-8069, CVE-2015-8070, CVE-2015-8071, CVE-2015-8401, CVE-2015-8402, CVE-2015-8403, CVE-2015-8404, CVE-2015-8405, CVE-2015-8406, CVE-2015-8410, CVE-2015-8411, CVE-2015-8412, CVE-2015-8413, CVE-2015-8414, CVE-2015-8420, CVE-2015-8421, CVE-2015-8422, CVE-2015-8423, CVE-2015-8424, CVE-2015-8425, CVE-2015-8426, CVE-2015-8427, CVE-2015-8428, CVE-2015-8429, CVE-2015-8430, CVE-2015-8431, CVE-2015-8432, CVE-2015-8433, CVE-2015-8434, CVE-2015-8435, CVE-2015-8436, CVE-2015-8437, CVE-2015-8441, CVE-2015-8442, CVE-2015-8447, CVE-2015-8448, CVE-2015-8449, CVE-2015-8450, CVE-2015-8452, CVE-2015-8454, CVE-2015-8655, CVE-2015-8821, and CVE-2015-8822. | 3 | 6 | NETWORK |
| CVE‑2015‑8652 | 2016‑03‑04 23:59:00 | HIGH (9) | Adobe Flash Player before 18.0.0.268 and 19.x and 20.x before 20.0.0.228 on Windows and OS X and before 11.2.202.554 on Linux, Adobe AIR before 20.0.0.204, Adobe AIR SDK before 20.0.0.204, and Adobe AIR SDK & Compiler before 20.0.0.204 allow attackers to execute arbitrary code or cause a denial of service (out-of-bounds read and memory corruption) via crafted MPEG-4 data, a different vulnerability than CVE-2015-8045, CVE-2015-8047, CVE-2015-8060, CVE-2015-8408, CVE-2015-8416, CVE-2015-8417, CVE-2015-8418, CVE-2015-8419, CVE-2015-8443, CVE-2015-8444, CVE-2015-8451, CVE-2015-8455, CVE-2015-8654, CVE-2015-8656, CVE-2015-8657, CVE-2015-8658, and CVE-2015-8820. | 3 | 6 | NETWORK |
| CVE‑2014‑3188 | 2014‑10‑08 10:55:06 | HIGH (10) | Google Chrome before 38.0.2125.101 and Chrome OS before 38.0.2125.101 do not properly handle the interaction of IPC and Google V8, which allows remote attackers to execute arbitrary code via vectors involving JSON data, related to improper parsing of an escaped index by ParseJsonObject in json-parser.h. | 0 | 0 | NETWORK |
| CVE‑2014‑3180 | 2019‑11‑06 20:15:10 | CRITICAL (9) | In kernel/compat.c in the Linux kernel before 3.17, as used in Google Chrome OS and other products, there is a possible out-of-bounds read. restart_syscall uses uninitialized data when restarting compat_sys_nanosleep. NOTE: this is disputed because the code path is unreachable | 4 | 5 | NETWORK |
| CVE‑2014‑1711 | 2014‑03‑16 14:06:46 | HIGH (8) | The GPU driver in the kernel in Google Chrome OS before 33.0.1750.152 allows remote attackers to cause a denial of service (out-of-bounds write) or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2014‑1710 | 2014‑03‑16 14:06:46 | HIGH (8) | The AsyncPixelTransfersCompletedQuery::End function in gpu/command_buffer/service/query_manager.cc in Google Chrome, as used in Google Chrome OS before 33.0.1750.152, does not check whether a certain position is within the bounds of a shared-memory segment, which allows remote attackers to cause a denial of service (GPU command-buffer memory corruption) or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2014‑1708 | 2014‑03‑16 14:06:46 | HIGH (10) | The boot implementation in Google Chrome OS before 33.0.1750.152 does not properly consider file persistence, which allows remote attackers to execute arbitrary code via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2014‑1707 | 2014‑03‑16 14:06:46 | HIGH (8) | Directory traversal vulnerability in CrosDisks in Google Chrome OS before 33.0.1750.152 has unspecified impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2014‑1706 | 2014‑03‑16 14:06:45 | HIGH (8) | crosh in Google Chrome OS before 33.0.1750.152 allows attackers to inject commands via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2014‑1568 | 2014‑09‑25 17:55:04 | HIGH (8) | Mozilla Network Security Services (NSS) before 3.16.2.1, 3.16.x before 3.16.5, and 3.17.x before 3.17.1, as used in Mozilla Firefox before 32.0.3, Mozilla Firefox ESR 24.x before 24.8.1 and 31.x before 31.1.1, Mozilla Thunderbird before 24.8.1 and 31.x before 31.1.2, Mozilla SeaMonkey before 2.29.1, Google Chrome before 37.0.2062.124 on Windows and OS X, and Google Chrome OS before 37.0.2062.120, does not properly parse ASN.1 values in X.509 certificates, which makes it easier for remote attackers to spoof RSA signatures via a crafted certificate, aka a "signature malleability" issue. | 0 | 0 | NETWORK |
| CVE‑2013‑2866 | 2013‑06‑19 20:55:01 | MEDIUM (4) | The Flash plug-in in Google Chrome before 27.0.1453.116, as used on Google Chrome OS before 27.0.1453.116 and separately, does not properly determine whether a user wishes to permit camera or microphone access by a Flash application, which allows remote attackers to obtain sensitive information from a machine's physical environment via a clickjacking attack, as demonstrated by an attack using a crafted Cascading Style Sheets (CSS) opacity property. | 0 | 0 | NETWORK |
| CVE‑2013‑2835 | 2013‑04‑16 20:55:02 | MEDIUM (5) | Google Chrome OS before 26.0.1410.57 does not properly enforce origin restrictions for the O3D and Google Talk plug-ins, which allows remote attackers to bypass the domain-whitelist protection mechanism via a crafted web site, a different vulnerability than CVE-2013-2834. | 0 | 0 | NETWORK |
| CVE‑2013‑2834 | 2013‑04‑16 20:55:02 | MEDIUM (5) | Google Chrome OS before 26.0.1410.57 does not properly enforce origin restrictions for the O3D and Google Talk plug-ins, which allows remote attackers to bypass the domain-whitelist protection mechanism via a crafted web site, a different vulnerability than CVE-2013-2835. | 0 | 0 | NETWORK |
| CVE‑2013‑2833 | 2013‑04‑16 20:55:02 | HIGH (10) | Use-after-free vulnerability in the O3D plug-in in Google Chrome OS before 26.0.1410.57 allows remote attackers to cause a denial of service or possibly have unspecified other impact via vectors related to improper management of ownership relationships involving Elements and DrawElements. | 0 | 0 | NETWORK |
| CVE‑2013‑2832 | 2013‑04‑16 20:55:02 | MEDIUM (5) | The Buffer::Set function in core/cross/buffer.cc in the O3D plug-in in Google Chrome OS before 26.0.1410.57 does not prevent uninitialized data from remaining in a buffer, which might allow remote attackers to obtain sensitive information via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2013‑0927 | 2013‑04‑10 16:55:05 | HIGH (8) | Google Chrome OS before 26.0.1410.57 relies on a Pango pango-utils.c read_config implementation that loads the contents of the .pangorc file in the user's home directory, and the file referenced by the PANGO_RC_FILE environment variable, which allows attackers to bypass intended access restrictions via crafted configuration data. | 0 | 0 | NETWORK |
| CVE‑2013‑0915 | 2013‑03‑18 15:55:12 | HIGH (10) | The GPU process in Google Chrome OS before 25.0.1364.173 allows attackers to cause a denial of service or possibly have unspecified other impact via vectors related to an "overflow." | 0 | 0 | NETWORK |
| CVE‑2012‑5129 | 2012‑12‑04 06:05:55 | HIGH (8) | Heap-based buffer overflow in the WebGL subsystem in Google Chrome OS before 23.0.1271.94 allows remote attackers to cause a denial of service (GPU process crash) or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2012‑4050 | 2012‑07‑24 19:55:03 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome OS before 21.0.1180.50 on the Cr-48 and Samsung Series 5 and 5 550 Chromebook platforms, and the Samsung Chromebox Series 3, have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2012‑3290 | 2012‑06‑07 19:55:10 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 20.0.1132.22 on the Acer AC700; Samsung Series 5, 5 550, and Chromebox 3; and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2012‑2864 | 2012‑08‑22 10:42:05 | HIGH (10) | Mesa, as used in Google Chrome before 21.0.1183.0 on the Acer AC700, Cr-48, and Samsung Series 5 and 5 550 Chromebook platforms, and the Samsung Chromebox Series 3, allows remote attackers to execute arbitrary code via unspecified vectors that trigger an "array overflow." | 0 | 0 | NETWORK |
| CVE‑2012‑1418 | 2012‑02‑29 11:55:06 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 17.0.963.60 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2012‑0695 | 2012‑01‑12 18:55:01 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 17.0.963.27 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑4719 | 2011‑12‑09 20:55:01 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 16.0.912.63 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑4548 | 2011‑11‑24 04:01:07 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 16.0.912.44 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑3421 | 2011‑09‑12 12:40:45 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 14.0.835.125 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑3420 | 2011‑09‑12 12:40:45 | HIGH (10) | Multiple unspecified vulnerabilities in Google Chrome before 14.0.835.157 on the Acer AC700, Samsung Series 5, and Cr-48 Chromebook platforms have unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑2171 | 2011‑05‑24 23:55:05 | HIGH (10) | Unspecified vulnerability in the dbugs package in Google Chrome OS before R12 0.12.433.38 Beta has unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑2170 | 2011‑05‑24 23:55:05 | MEDIUM (4) | Google Chrome OS before R12 0.12.433.38 Beta, when Guest mode is enabled, does not prevent changes on the about:flags page, which has unspecified impact and local attack vectors. | 0 | 0 | LOCAL |
| CVE‑2011‑2169 | 2011‑05‑24 23:55:05 | HIGH (7) | Google Chrome OS before R12 0.12.433.38 Beta allows local users to gain privileges by creating a /var/lib/chromeos-aliases.conf file and placing commands in it. | 0 | 0 | LOCAL |
| CVE‑2011‑1306 | 2011‑03‑08 21:59:34 | HIGH (10) | Unspecified vulnerability in the Scratchpad application in Google Chrome OS before R10 0.10.156.46 Beta has unknown impact and attack vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑1042 | 2011‑02‑18 17:00:46 | MEDIUM (4) | Use-after-free vulnerability in flimflamd in flimflam in Google Chrome OS before 0.9.130.14 Beta allows user-assisted remote attackers to cause a denial of service (daemon crash) by providing the name of a hidden WiFi network that does not respond to connection attempts. | 0 | 0 | NETWORK |
| CVE‑2011‑0611 | 2011‑04‑13 14:55:01 | HIGH (9) | Adobe Flash Player before 10.2.154.27 on Windows, Mac OS X, Linux, and Solaris and 10.2.156.12 and earlier on Android; Adobe AIR before 2.6.19140; and Authplay.dll (aka AuthPlayLib.bundle) in Adobe Reader 9.x before 9.4.4 and 10.x through 10.0.1 on Windows, Adobe Reader 9.x before 9.4.4 and 10.x before 10.0.3 on Mac OS X, and Adobe Acrobat 9.x before 9.4.4 and 10.x before 10.0.3 on Windows and Mac OS X allow remote attackers to execute arbitrary code or cause a denial of service (application crash) via crafted Flash content; as demonstrated by a Microsoft Office document with an embedded .swf file that has a size inconsistency in a "group of included constants," object type confusion, ActionScript that adds custom functions to prototypes, and Date objects; and as exploited in the wild in April 2011. | 3 | 6 | NETWORK |
| CVE‑2011‑0609 | 2011‑03‑15 17:55:04 | HIGH (8) | Unspecified vulnerability in Adobe Flash Player 10.2.154.13 and earlier on Windows, Mac OS X, Linux, and Solaris; 10.1.106.16 and earlier on Android; Adobe AIR 2.5.1 and earlier; and Authplay.dll (aka AuthPlayLib.bundle) in Adobe Reader and Acrobat 9.x through 9.4.2 and 10.x through 10.0.1 on Windows and Mac OS X, allows remote attackers to execute arbitrary code or cause a denial of service (application crash) via crafted Flash content, as demonstrated by a .swf file embedded in an Excel spreadsheet, and as exploited in the wild in March 2011. | 2 | 6 | LOCAL |
| CVE‑2011‑0485 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle speech data, which allows remote attackers to execute arbitrary code via unspecified vectors that lead to a "stale pointer." | 0 | 0 | NETWORK |
| CVE‑2011‑0484 | 2011‑01‑14 17:00:03 | HIGH (8) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly perform DOM node removal, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors that lead to a "stale rendering node." | 0 | 0 | NETWORK |
| CVE‑2011‑0483 | 2011‑01‑14 17:00:03 | MEDIUM (5) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly perform a cast of an unspecified variable during handling of video, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑0482 | 2011‑01‑14 17:00:03 | MEDIUM (4) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly perform a cast of an unspecified variable during handling of anchors, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via a crafted HTML document. | 0 | 0 | NETWORK |
| CVE‑2011‑0481 | 2011‑01‑14 17:00:03 | HIGH (9) | Buffer overflow in Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 allows remote attackers to cause a denial of service or possibly have unspecified other impact via vectors related to PDF shading. | 0 | 0 | NETWORK |
| CVE‑2011‑0480 | 2011‑01‑14 17:00:03 | HIGH (9) | Multiple buffer overflows in vorbis_dec.c in the Vorbis decoder in FFmpeg, as used in Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344, allow remote attackers to cause a denial of service (memory corruption and application crash) or possibly have unspecified other impact via a crafted WebM file, related to buffers for (1) the channel floor and (2) the channel residue. | 0 | 0 | NETWORK |
| CVE‑2011‑0479 | 2011‑01‑14 17:00:03 | HIGH (8) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly interact with extensions, which allows remote attackers to cause a denial of service via a crafted extension that triggers an uninitialized pointer. | 0 | 0 | NETWORK |
| CVE‑2011‑0478 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle SVG use elements, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors that lead to a "stale pointer." | 0 | 0 | NETWORK |
| CVE‑2011‑0477 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle a mismatch in video frame sizes, which allows remote attackers to cause a denial of service (incorrect memory access) or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑0476 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 allow remote attackers to cause a denial of service (stack memory corruption) or possibly have unspecified other impact via a PDF document that triggers an out-of-memory error. | 0 | 0 | NETWORK |
| CVE‑2011‑0475 | 2011‑01‑14 17:00:03 | HIGH (9) | Use-after-free vulnerability in Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 allows remote attackers to cause a denial of service or possibly have unspecified other impact via a PDF document. | 0 | 0 | NETWORK |
| CVE‑2011‑0474 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle Cascading Style Sheets (CSS) token sequences in conjunction with cursors, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors that lead to a "stale pointer." | 0 | 0 | NETWORK |
| CVE‑2011‑0473 | 2011‑01‑14 17:00:03 | HIGH (10) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle Cascading Style Sheets (CSS) token sequences in conjunction with CANVAS elements, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors that lead to a "stale pointer." | 0 | 0 | NETWORK |
| CVE‑2011‑0472 | 2011‑01‑14 17:00:03 | HIGH (9) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle the printing of PDF documents, which allows user-assisted remote attackers to cause a denial of service (application crash) or possibly have unspecified other impact via a multi-page document. | 0 | 0 | NETWORK |
| CVE‑2011‑0471 | 2011‑01‑14 17:00:03 | HIGH (10) | The node-iteration implementation in Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 does not properly handle pointers, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors. | 0 | 0 | NETWORK |
| CVE‑2011‑0470 | 2011‑01‑14 17:00:03 | MEDIUM (5) | Google Chrome before 8.0.552.237 and Chrome OS before 8.0.552.344 do not properly handle extensions notification, which allows remote attackers to cause a denial of service (application crash) via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2010‑4578 | 2010‑12‑22 01:00:03 | HIGH (8) | Google Chrome before 8.0.552.224 and Chrome OS before 8.0.552.343 do not properly perform cursor handling, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via unknown vectors that lead to "stale pointers." | 0 | 0 | NETWORK |
| CVE‑2010‑4577 | 2010‑12‑22 01:00:03 | HIGH (8) | The CSSParser::parseFontFaceSrc function in WebCore/css/CSSParser.cpp in WebKit, as used in Google Chrome before 8.0.552.224, Chrome OS before 8.0.552.343, webkitgtk before 1.2.6, and other products does not properly parse Cascading Style Sheets (CSS) token sequences, which allows remote attackers to cause a denial of service (out-of-bounds read) via a crafted local font, related to "Type Confusion." | 4 | 4 | NETWORK |
| CVE‑2010‑4576 | 2010‑12‑22 01:00:03 | MEDIUM (5) | browser/worker_host/message_port_dispatcher.cc in Google Chrome before 8.0.552.224 and Chrome OS before 8.0.552.343 does not properly handle certain postMessage calls, which allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via crafted JavaScript code that creates a web worker. | 0 | 0 | NETWORK |
| CVE‑2010‑4575 | 2010‑12‑22 01:00:03 | MEDIUM (4) | The ThemeInstalledInfoBarDelegate::Observe function in browser/extensions/theme_installed_infobar_delegate.cc in Google Chrome before 8.0.552.224 and Chrome OS before 8.0.552.343 does not properly handle incorrect tab interaction by an extension, which allows user-assisted remote attackers to cause a denial of service (application crash) via a crafted extension. | 0 | 0 | NETWORK |
| CVE‑2010‑4574 | 2010‑12‑22 01:00:03 | HIGH (8) | The Pickle::Pickle function in base/pickle.cc in Google Chrome before 8.0.552.224 and Chrome OS before 8.0.552.343 on 64-bit Linux platforms does not properly perform pointer arithmetic, which allows remote attackers to bypass message deserialization validation, and cause a denial of service or possibly have unspecified other impact, via invalid pickle data. | 0 | 0 | NETWORK |

Get the IT stuff done that nobody wants to do.
Patch more applications, achieve compliance, and prevent problems while reducing stress with Lavawall®.
Security First
A security tool by security auditors. From Passkeys and Argon2i to source validation and MVSP principles, Lavawall® has you covered.
Constant Improvement
More features and more security added nearly every day.
More patchable programs added every week
While Ninite and other patching tools have had the same patch offerings for decades, we're monitoring stats to keep adding the most useful prorgams.
Details matter
From wrapping TLS communications in extra encryption and uninstalling remote support tools when they aren't used to detailed statistical analysis of system and network performance, Lavawall® goes in-depth.
Chromium extensions and Notification Validation
Lavawall® goes beyond patches and breach detection. We also monitor for risky Chromium extensions and allowed notifications that might be part of a phishing or ransomware attack.
Extended Cloud Security
Extend the security features of Cloudflare, Microsoft, Google, Sophos, and other cloud providers to create a Lavawall® of protection
Secure Remote Management
Even if you used breached remote management tools like ScreenConnect through Lavawall® when it was vulnerable, your computers stayed safe because we only install the agent when it needs to be used.
Integrations and automation
Easily deploy, monitor, and analyze security tools like Huntress, AutoElevate, and Sophos. Magically gain details from ZenDesk, ConnectWise, Datto, Panorama9, Microsoft, and Google.
Human and automated support
Get immediate fixes, user notifications, admin notifications -- and even security-certified human level 3 support when our advanced statistical analysis confirms a problem or anomaly.
| 2024‑10‑30 | 0.12.8.195 | Mac update refinements |
| 2024‑10‑25 | 0.12.3.190 | |
| 2024‑10‑21 | 0.12.0.187 | Macos implementaiton, linux and windows improvements |
| 2024‑10‑16 | 0.11.128.186 | Linux stats and system information improvements, improvements for application shutdown |
| 2024‑09‑12 | 0.11.113.171 | CPU Optimizations and Packages reliability improvements |
| 2024‑09‑05 | 0.11.106.164 | Phased deployment enhancements |
| 2024‑09‑04 | 0.11.103.161 | |
| 2024‑09‑02 | 0.11.102.160 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑30 | 0.11.99.157 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑29 | 0.11.98.156 | CPU utilization and console event optimization |
| 2024‑08‑28 | 0.11.97.155 | Reliability to detect unusual updates like redistributables. |
| 2024‑08‑27 | 0.11.96.154 | |
| 2024‑08‑26 | 0.11.95.153 | Faster response for reboot requests |
| 2024‑08‑20 | 0.11.92.150 | Additional package upgrade pre-requisites |
| 2024‑08‑15 | 0.11.89.147 | |
| 2024‑08‑06 | 0.11.87.145 | |
| 2024‑07‑26 | 0.11.83.141 | Add resiliency for MAC duplicates and uptime |
| 2024‑07‑25 | 0.11.82.140 | Changes to facilitate cross-platform use. Bitlocker and Windows key refinements |
| 2024‑07‑15 | 0.11.80.138 | Antivirus and temperature added to configuration checks |
| 2024‑07‑15 | 0.11.79.137 | Add configuration checks for execution policy and secure boot |
| 2024‑07‑11 | 0.11.77.135 | load balancing refinements |
| 2024‑07‑10 | 0.11.76.134 | Add additional load balancing and data residency capabilities, add randomness to recurring task timings to decrease server load |
| 2024‑07‑05 | 0.11.74.132 | changes to graph and residual work on user imporsonation |
| 2024‑07‑04 | 0.11.73.131 | Add configuration checks for execution policy and secure boot. |
| 2024‑07‑03 | 0.11.72.130 | Enhanced event log monitoring |
| 2024‑07‑02 | 0.11.71.129 | Add details to Windows updates, enhanced risk metrics for application patches |
| 2024‑06‑19 | 0.11.65.123 | Update resiliancy and garbage collection |
| 2024‑06‑13 | 0.11.60.118 | Enhanced logging |
| 2024‑06‑12 | 0.11.55.113 | Include the primary drive serial number; MAC addresses for built-in wireless, Bluetooth, and ethernet into the device hash to restore uninstalled and reinstalled devices in cases where the motherboard serial is not unique |
| 2024‑06‑07 | 0.11.54.112 | Patch and package uninstall data addition |
| 2024‑06‑05 | 0.11.47.105 | refine per-user registry application listing |
| 2024‑06‑02 | 0.11.45.103 | uninstall and reinstall refinements, refine local logging, refine self-update and uninstall timing |
| 2024‑05‑30 | 0.11.21.79 | various bug fixes and improvements |
| 2024‑05‑28 | 0.11.16.74 | Error logging, registration, and uninstall improvements. |
| 2024‑05‑24 | 0.11.14.72 | applied changes for devices and login commands, changes for registration as well |
| 2024‑05‑22 | 0.11.13.71 | Add Windows computer model, improve Operating System parsing |
| 2024‑05‑21 | 0.11.11.69 | Added additional states for Windows update, flexibility for non-standard program file configurations, support for network diagrams at the switch level, details for Windows editions |
| 2024‑05‑21 | 0.11.10.68 | Add specific cases for Defender patterns and Composer versions. |
| 2024‑05‑17 | 0.11.3.61 | Change Log storage location to c:\program files\Lavawall |
| 2024‑05‑17 | 0.11.1.59 | self-update improvements. |
| 2024‑05‑16 | 0.8.0.55 | error log reporting and management. |
| 2024‑05‑15 | 0.7.0.54 | Websocket resiliency improvements |
| 2024‑05‑09 | 0.6.0.53 | Error log reporting and management. |
| 2024‑05‑01 | 0.5.44.52 | Even more improvements to scheduler |
| 2024‑04‑24 | 0.5.41.49 | Install compatibility with Sandbox |
| 2024‑04‑22 | 0.5.21.29 | Project property changes to enable automated compilation with new features. |
| 2024‑04‑20 | 0.5.20.28 | Add motherboard serial number and company reassignment |
| 2024‑04‑11 | 0.5.4.12 | Automate release notes as part of build process |
| 2024‑04‑03 | 0.5.3.11 | Websocket and service enhancements |
| 2024‑03‑21 | 0.5.2.10 | Enhance zip file validation |
NOTE: changes after June 2024 are incorportated into the Windows Changelog as the codebases for Windows, Linux, and Mac were combined
| 2024‑05‑20 | 253 | Added cleanup of old .json files during a re-install |
| 2024‑05‑13 | 252 | Added apt-get update to install |
| 2024‑05‑06 | 248 | Allow restart to use /var/run/reboot-required if needrestart is not installed |
| 2024‑04‑22 | 239 | Improve internal update and version tracking |
| 2024‑04‑15 | 235 | Add support for Yum packages |
| 2024‑04‑08 | 233 | Align patching with Windows patch reporting |
| 2024‑04‑02 | 228 | Add support for needrestart |
| 2024‑03‑04 | 224 | Schedule restarts |
| 2024‑03‑25 | 221 | Add support for apt packages |
| 2024‑03‑18 | 212 | Implement release management |
| 2024‑03‑11 | 202 | Add user login monitoring |
| 2024‑03‑04 | 189 | Enhance installation reliability |
| 2024‑02‑26 | 187 | Exapand triggers to identify if the instance needs to be restarted |
| 2024‑02‑19 | 146 | Improve compatibility for non-AWS instances |
| 2024‑02‑14 | 138 | Add self-uninstall capabilities |
| 2024‑02‑12 | 135 | Enhance scheduling flexibility |
| 2024‑02‑07 | 132 | Add kernel version tracking |
| 2024‑02‑05 | 124 | Add device hash to cryptographic self-update script validation |
| 2024‑01‑29 | 107 | Enhance encryption of patch data |
| 2024‑01‑22 | 98 | Improve how available storage is calculated |
| 2024‑01‑15 | 97 | Move initial tasks from installation file to sub scripts |
| 2024‑05‑21 | 91 | Improve multi-distribution compatibility |
| 2024‑05‑21 | 79 | Improve encryption reliability |
| 2023‑12‑11 | 68 | Enhance cryptographic validation of new scripts before updating |
| 2023‑11‑20 | 62 | Add inner layer of AES encryption in case TLS inspection doesn't allow for a secure connection |
| 2023‑11‑27 | 56 | Additional base cases for resiliancy |
| 2023‑11‑20 | 54 | Additional headers added to authentication process during installation. |
| 2023‑11‑20 | 53 | Enhanced key management |
| 2023‑11‑15 | 51 | Add insecure installation parameter to allow installation in environments with TLS inspection or other machine-in-the-middle situations. |
| 2023‑11‑06 | 42 | Enhance redundant encryption during installation. |
| 2023‑10‑30 | 33 | Improve install-over compatibility |
| 2023‑10‑23 | 18 | Add reboot configuration and scheduling |
| 2023‑10‑23 | 17 | Add self-updating functionality. |
| 2023‑10‑16 | 15 | Add Linux patching information for apt |
| 2023‑10‑09 | 14 | Collect system information |
| 2023‑10‑09 | 13 | Add Linux distribution information |
| 2023‑09‑30 | 12 | Add memory monitoring |
| 2023‑09‑30 | 10 | Add hardware information |
| 2023‑09‑23 | 9 | Add AWS information |
| 2023‑09‑23 | 8 | Add customized schedule capability for configuration updates |
| 2023‑09‑23 | 7 | Add support for package monitoring using package and dpkg logs |
| 2023‑09‑16 | 6 | Add storage data configuration gathering |
| 2023‑09‑16 | 5 | Add CPU information |
Lavawall® was built from the ground up with these concerns and the Minimum Viable Secure Product requirements in mind.
Some of the controls we implemented include:
- PassKeys as the preferred primary authentication at no additional cost
- Single Sign-on using modern, maintained, and industry-standard protocols for all customers at no additional cost
- Multi-Factor Authentication as a non-negotiable default
- Encrypting communications the same way as TLS again within the TLS tunnel, so we can allow TLS inspection without breaking like Huntress or disclosing security vulnerabilities to eavesdroppers.
- Encouraging external vulnerability reports and customer testing
- Passwords checked against popular disclosed passwords, hashed before they leave your computer, and then stored using Argon2id
- Not requiring the use of passwords at all. We consider them a temporary backup authentication in case you can't use passkeys or SSO.
Lavawall® databases and front-end systems are hosted with AWS in Montréal, Québec, Canada.
We send emails through AWS in Ireland and dedicated servers in Calgary, Alberta, Canada.
We send text messages for additional identity verification through Twilio in the United States.
We store executables and pass requests through Cloudflare at your nearest edge location.
We use Cloudflare for risk management, turnstile, and web application firewall services.
We use LeadPages for landing pages.
We use Google and Facebook for analytics on our public-facing pages, but they do not have access to the console.
We integrate with third-party tools, such as Microsoft, Google, Huntress, Screen Connect, Axcient, and Datto in their respective locations. However, you must initiate these integrations through single sign-on or by enabling them in your Lavawall® console.
Active security by design
Lavawall® is under active development with the latest release on
5+
Interfaces
350+
Monitored Applications
7+
System Metrics
Actively manage your IT with Lavawall®
Patching
Updates Beyond Windows
Lavawall® prevents the 80% of breaches and failed audits due to missing patches and updates.
You can reduce application patching delays from 67 days to nearly immediate with the 350+ applications that Lavawall® monitors and patches.
Patch release monitoring
Monitor everything without having to select packages or “managed applications”
Patch impact classification
Standard and optional Windows patches
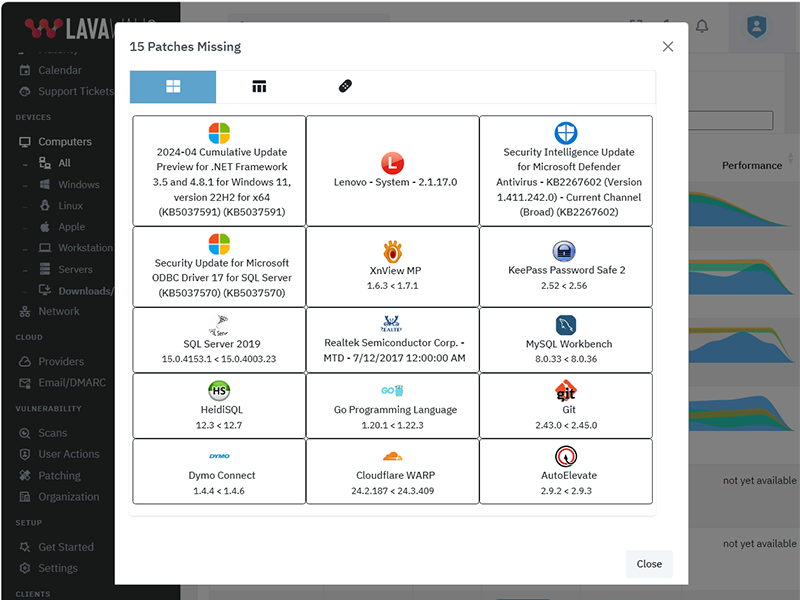
The above listing includes products that Lavawall® monitors through public information and/or proprietary statistical analysis.
Although we do have a partner relationship with some of the listed products and companies, they do not necessarily endorse Lavawall® or have integrations with our systems.
Learn More
Flexible Term; Flexible Service
Flexibility for your dynamic business
You need to get your arms around compliance and security and don't want to get locked into “high watermark” monthly invoices or multi-year contracts.
Pay-as-you-need monthly pricing
DIY, full management, and coaching options
CMMI, PCI, SOC2, Canadian Cybersecurity, Minimum Viable Secure Product, and other compliance support
Choose the plan that's right for you
Simple pricing. No hidden fees. Advanced features for you business.
Month
Annual
Get 2 months free with Annual!
DIY
Security-focused RMM
C$3.25 /computer/Month
C$32.50 /computer/Year
-
1 computer
or 1 of the following cloud integrations:
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
(each integration counts as 1 computer) -
50+ application patches
-
30-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR: C$13.50/desktopSophos MDR: C$162/desktop
-
Huntress: C$5.40/deviceHuntress: C$64.80/device
-
Available white-label support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
Managed Security & Support
Unlimited end-user support
C$160 /user/Month
C$1,600 /user/Year
-
1 computer/user
Additional devices charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
350+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall® support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for end users
-
Level 3+ IT support for IT
-
Weekly IT coaching sessions
-
Automatic discount and upgrade to Support & Coaching after 15 users
Support & Coaching
Improve your IT performance
$2,250 /Month
$22,500 /Year
-
25 computers included
Additional computers charged at DIY prices -
AWS, Axcient, Connectwise, Datto, Google, Huntress, M365, Sophos Central integrations
-
350+ application patches
-
90-day Logs
-
Security configuration monitoring
-
Anomaly detection
-
CMMI, MVSP, CyberCanda compliance
-
Lavawall®-only support
-
Sophos MDR Essentials
-
Huntress
-
White-label email and phone support for 15 users included Additional: C$150/user Additional: C$1,500/user
-
L3 IT support for IT
-
Weekly IT coaching sessions
Frequently Asked Questions
If you can not find answer to your question in our FAQ, you can always contact us or email us. We will answer you shortly!
General Questions
- Two years after a missing Plex Media Server led to the LastPass breach, the
Remote Monitorign and Management (RMM) tools availabel for Manged IT Service Providers (MSPs)
still didn't monitor for it.
Going through industry-specific applications, we noticed many were missing from the big RMM and patching providers. MSPs, insurance providers, and organizations that put their cleints at risk need to know about these risks, which lead to the largest number of critical audit findings and breaches - After 20 years of writing the same audit findings about system configurations, Payment Card Industry (PCI) compliance, and missing patches, our technical co-founder wanted to make it easier fo avoid these findings
- The existing risk visibility tools for insurance underwriters took a shallow look at Internet-facing risks. They -- along with all businesses -- need a deeper view of the threats that could actually lead to breaches.
- Domain risks
- Operating System (OS) patches
- Application patches
- Network vulnerabilities
- Cloud vulnerabilities
- OS configurations
- Axcient*
- Cloudflare
- Connectwise Screen Connect
- Datto RMM
- FreshDesk*
- Huntress
- Microsoft 365
- Panorama9
- ZenDesk
You can use your own logo for the console and notifications. You can also use a CNAME to automatically brand your console.
Note: you cannot currently re-proxy the CNAME to Lavawall® through Cloudflare.
Lavawall® supports the following operating systems:
Lavawall® does not currently support non systemd distributions, such as Devuan, Artix Linux, PCLinuxOS, OpenWRT, and DD-WRT. However, we will support them by the end of 2024.
In June 2024, we combined the Windows and Linux systems for a consistent experience. This added support for RedHat and MacOS.
Privacy & Security
However, we do allow passwords and use passwords as part of the zero-knowledge encryption for your clients' sensitive data, such as Bitlocker keys and Personally-Identifiable Information (PII).
These passwords use Argon2id slow hashes with individual salts and peppers.
We have added an additional secure tunnel that mimics the TLS process within the public TLS tunnel. This extra tunnel provides authentication and privacy for the workstations and the Lavawall® servers to prevent attacks such as the one that took down Solar Winds.
Remote access is not enabled for read-only and audit situations.
Get In Touch
Have a quick question and don't want to talk? Send us a quick note with the form below and we'll reply within one business day.
NW Calgary:
ThreeShield Information Security Corporation
600 Crowfoot Crescent N.W., Suite 340
Calgary, Alberta
T3G 0B4
SE Calgary:
ThreeShield Information Security Corporation
105, 11500 - 29th St. SE
Calgary, Alberta
T2Z 3W9
Canada