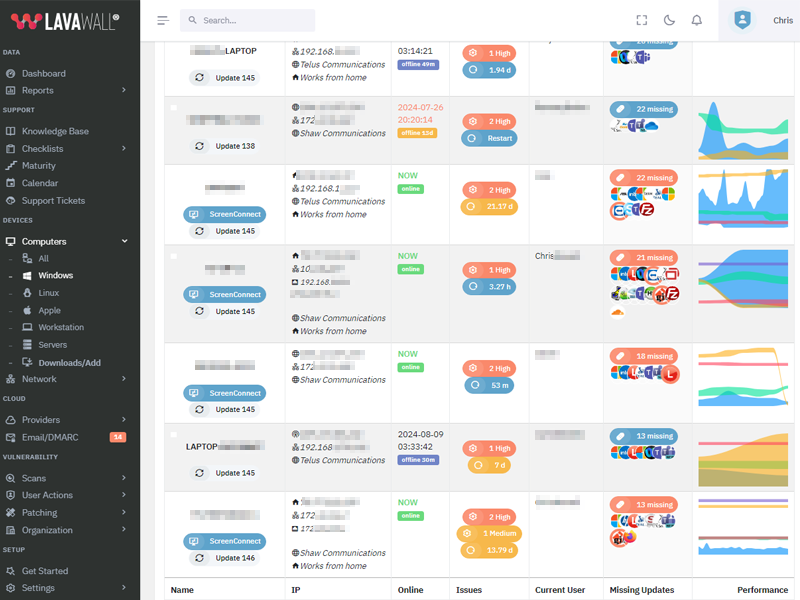
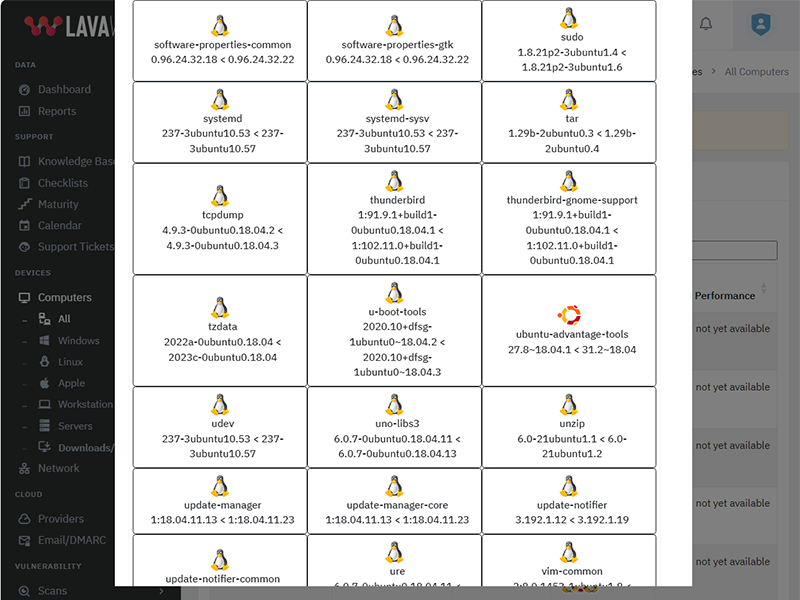
Update VLC to version 3.0.21
What patches are you missing?
CVE Vulnerabilities for VLC
| CVE | Published | Severity | Details | Exploitability | Impact | Vector |
| CVE‑2023‑47360 | 2023‑11‑07 16:15:29 | HIGH (8) | Videolan VLC prior to version 3.0.20 contains an Integer underflow that leads to an incorrect packet length. | 4 | 4 | NETWORK |
| CVE‑2023‑47359 | 2023‑11‑07 16:15:29 | CRITICAL (10) | Videolan VLC prior to version 3.0.20 contains an incorrect offset read that leads to a Heap-Based Buffer Overflow in function GetPacket() and results in a memory corruption. | 4 | 6 | NETWORK |
| CVE‑2023‑46814 | 2023‑11‑22 05:15:08 | HIGH (8) | A binary hijacking vulnerability exists within the VideoLAN VLC media player before 3.0.19 on Windows. The uninstaller attempts to execute code with elevated privileges out of a standard user writable location. Standard users may use this to gain arbitrary code execution as SYSTEM. | 2 | 6 | LOCAL |
| CVE‑2022‑41325 | 2022‑12‑06 16:15:11 | HIGH (8) | An integer overflow in the VNC module in VideoLAN VLC Media Player through 3.0.17.4 allows attackers, by tricking a user into opening a crafted playlist or connecting to a rogue VNC server, to crash VLC or execute code under some conditions. | 2 | 6 | LOCAL |
| CVE‑2021‑25804 | 2021‑07‑26 17:15:08 | HIGH (8) | A NULL-pointer dereference in "Open" in avi.c of VideoLAN VLC Media Player 3.0.11 can a denial of service (DOS) in the application. | 4 | 4 | NETWORK |
| CVE‑2021‑25803 | 2021‑07‑26 17:15:08 | HIGH (7) | A buffer overflow vulnerability in the vlc_input_attachment_New component of VideoLAN VLC Media Player 3.0.11 allows attackers to cause an out-of-bounds read via a crafted .avi file. | 2 | 5 | LOCAL |
| CVE‑2021‑25802 | 2021‑07‑26 17:15:08 | HIGH (7) | A buffer overflow vulnerability in the AVI_ExtractSubtitle component of VideoLAN VLC Media Player 3.0.11 allows attackers to cause an out-of-bounds read via a crafted .avi file. | 2 | 5 | LOCAL |
| CVE‑2021‑25801 | 2021‑07‑26 17:15:08 | HIGH (7) | A buffer overflow vulnerability in the __Parse_indx component of VideoLAN VLC Media Player 3.0.11 allows attackers to cause an out-of-bounds read via a crafted .avi file. | 2 | 5 | LOCAL |
| CVE‑2020‑26664 | 2021‑01‑08 18:15:13 | HIGH (8) | A vulnerability in EbmlTypeDispatcher::send in VideoLAN VLC media player 3.0.11 allows attackers to trigger a heap-based buffer overflow via a crafted .mkv file. | 2 | 6 | LOCAL |
| CVE‑2020‑13428 | 2020‑06‑08 19:15:11 | HIGH (8) | A heap-based buffer overflow in the hxxx_AnnexB_to_xVC function in modules/packetizer/hxxx_nal.c in VideoLAN VLC media player before 3.0.11 for macOS/iOS allows remote attackers to cause a denial of service (application crash) or execute arbitrary code via a crafted H.264 Annex-B video (.avi for example) file. | 2 | 6 | LOCAL |
| CVE‑2019‑5460 | 2019‑07‑30 21:15:12 | MEDIUM (6) | Double Free in VLC versions <= 3.0.6 leads to a crash. | 2 | 4 | LOCAL |
| CVE‑2019‑5459 | 2019‑07‑30 21:15:12 | HIGH (7) | An Integer underflow in VLC Media Player versions < 3.0.7 leads to an out-of-band read. | 2 | 5 | LOCAL |
| CVE‑2019‑5439 | 2019‑06‑13 16:29:02 | MEDIUM (4) | A Buffer Overflow in VLC Media Player < 3.0.7 causes a crash which can possibly be further developed into a remote code execution exploit. | 0 | 0 | NETWORK |
| CVE‑2019‑19721 | 2020‑05‑15 18:15:13 | HIGH (8) | An off-by-one error in the DecodeBlock function in codec/sdl_image.c in VideoLAN VLC media player before 3.0.9 allows remote attackers to cause a denial of service (memory corruption) via a crafted image file. NOTE: this may be related to the SDL_Image product. | 2 | 6 | LOCAL |
| CVE‑2019‑18278 | 2019‑10‑23 14:15:11 | HIGH (8) | When executing VideoLAN VLC media player 3.0.8 with libqt on Windows, Data from a Faulting Address controls Code Flow starting at libqt_plugin!vlc_entry_license__3_0_0f+0x00000000003b9aba. NOTE: the VideoLAN security team indicates that they have not been contacted, and have no way of reproducing this issue. | 2 | 6 | LOCAL |
| CVE‑2019‑14970 | 2019‑08‑29 19:15:14 | MEDIUM (7) | A vulnerability in mkv::event_thread_t in VideoLAN VLC media player 3.0.7.1 allows remote attackers to trigger a heap-based buffer overflow via a crafted .mkv file. | 0 | 0 | NETWORK |
| CVE‑2019‑14778 | 2019‑08‑29 19:15:14 | MEDIUM (7) | The mkv::virtual_segment_c::seek method of demux/mkv/virtual_segment.cpp in VideoLAN VLC media player 3.0.7.1 has a use-after-free. | 0 | 0 | NETWORK |
| CVE‑2019‑14777 | 2019‑08‑29 19:15:13 | MEDIUM (7) | The Control function of demux/mkv/mkv.cpp in VideoLAN VLC media player 3.0.7.1 has a use-after-free. | 0 | 0 | NETWORK |
| CVE‑2019‑14776 | 2019‑08‑29 19:15:13 | MEDIUM (7) | A heap-based buffer over-read exists in DemuxInit() in demux/asf/asf.c in VideoLAN VLC media player 3.0.7.1 via a crafted .mkv file. | 0 | 0 | NETWORK |
| CVE‑2019‑14535 | 2019‑08‑29 18:15:12 | MEDIUM (7) | A divide-by-zero error exists in the SeekIndex function of demux/asf/asf.c in VideoLAN VLC media player 3.0.7.1. As a result, an FPE can be triggered via a crafted WMV file. | 0 | 0 | NETWORK |
| CVE‑2019‑14534 | 2019‑08‑29 19:15:13 | MEDIUM (4) | In VideoLAN VLC media player 3.0.7.1, there is a NULL pointer dereference at the function SeekPercent of demux/asf/asf.c that will lead to a denial of service attack. | 0 | 0 | NETWORK |
| CVE‑2019‑14533 | 2019‑08‑29 19:15:13 | MEDIUM (7) | The Control function of demux/asf/asf.c in VideoLAN VLC media player 3.0.7.1 has a use-after-free. | 0 | 0 | NETWORK |
| CVE‑2019‑14498 | 2019‑08‑29 18:15:12 | MEDIUM (7) | A divide-by-zero error exists in the Control function of demux/caf.c in VideoLAN VLC media player 3.0.7.1. As a result, an FPE can be triggered via a crafted CAF file. | 0 | 0 | NETWORK |
| CVE‑2019‑14438 | 2019‑08‑29 18:15:12 | MEDIUM (7) | A heap-based buffer over-read in xiph_PackHeaders() in modules/demux/xiph.h in VideoLAN VLC media player 3.0.7.1 allows remote attackers to trigger a heap-based buffer over-read via a crafted .ogg file. | 0 | 0 | NETWORK |
| CVE‑2019‑14437 | 2019‑08‑29 18:15:12 | MEDIUM (7) | The xiph_SplitHeaders function in modules/demux/xiph.h in VideoLAN VLC media player 3.0.7.1 does not check array bounds properly. As a result, a heap-based buffer over-read can be triggered via a crafted .ogg file. | 0 | 0 | NETWORK |
| CVE‑2019‑13962 | 2019‑07‑18 20:15:12 | CRITICAL (10) | lavc_CopyPicture in modules/codec/avcodec/video.c in VideoLAN VLC media player through 3.0.7 has a heap-based buffer over-read because it does not properly validate the width and height. | 4 | 6 | NETWORK |
| CVE‑2019‑13615 | 2019‑07‑16 17:15:13 | MEDIUM (4) | libebml before 1.3.6, as used in the MKV module in VideoLAN VLC Media Player binaries before 3.0.3, has a heap-based buffer over-read in EbmlElement::FindNextElement. | 0 | 0 | NETWORK |
| CVE‑2019‑13602 | 2019‑07‑14 21:15:11 | HIGH (8) | An Integer Underflow in MP4_EIA608_Convert() in modules/demux/mp4/mp4.c in VideoLAN VLC media player through 3.0.7.1 allows remote attackers to cause a denial of service (heap-based buffer overflow and crash) or possibly have unspecified other impact via a crafted .mp4 file. | 2 | 6 | LOCAL |
| CVE‑2019‑12874 | 2019‑06‑18 18:15:11 | HIGH (8) | An issue was discovered in zlib_decompress_extra in modules/demux/mkv/util.cpp in VideoLAN VLC media player 3.x through 3.0.7. The Matroska demuxer, while parsing a malformed MKV file type, has a double free. | 0 | 0 | NETWORK |
| CVE‑2018‑19857 | 2018‑12‑05 11:29:06 | MEDIUM (6) | The CAF demuxer in modules/demux/caf.c in VideoLAN VLC media player 3.0.4 may read memory from an uninitialized pointer when processing magic cookies in CAF files, because a ReadKukiChunk() cast converts a return value to an unsigned int even if that value is negative. This could result in a denial of service and/or a potential infoleak. | 0 | 0 | NETWORK |
| CVE‑2018‑11529 | 2018‑07‑11 16:29:01 | MEDIUM (7) | VideoLAN VLC media player 2.2.x is prone to a use after free vulnerability which an attacker can leverage to execute arbitrary code via crafted MKV files. Failed exploit attempts will likely result in denial of service conditions. | 0 | 0 | NETWORK |
| CVE‑2018‑11516 | 2018‑05‑28 16:29:00 | HIGH (9) | The vlc_demux_chained_Delete function in input/demux_chained.c in VideoLAN VLC media player 3.0.1 allows remote attackers to cause a denial of service (heap corruption and application crash) or possibly have unspecified other impact via a crafted .swf file. | 3 | 6 | NETWORK |
| CVE‑2017‑9301 | 2017‑05‑29 19:29:00 | MEDIUM (7) | plugins\audio_filter\libmpgatofixed32_plugin.dll in VideoLAN VLC media player 2.2.4 allows remote attackers to cause a denial of service (invalid read and application crash) or possibly have unspecified other impact via a crafted file. | 0 | 0 | NETWORK |
| CVE‑2017‑9300 | 2017‑05‑29 19:29:00 | MEDIUM (7) | plugins\codec\libflac_plugin.dll in VideoLAN VLC media player 2.2.4 allows remote attackers to cause a denial of service (heap corruption and application crash) or possibly have unspecified other impact via a crafted FLAC file. | 0 | 0 | NETWORK |
| CVE‑2017‑8313 | 2017‑05‑23 21:29:00 | MEDIUM (4) | Heap out-of-bound read in ParseJSS in VideoLAN VLC before 2.2.5 due to missing check of string termination allows attackers to read data beyond allocated memory and potentially crash the process via a crafted subtitles file. | 0 | 0 | NETWORK |
| CVE‑2017‑8312 | 2017‑05‑23 21:29:00 | MEDIUM (4) | Heap out-of-bound read in ParseJSS in VideoLAN VLC due to missing check of string length allows attackers to read heap uninitialized data via a crafted subtitles file. | 0 | 0 | NETWORK |
| CVE‑2017‑8311 | 2017‑05‑23 21:29:00 | MEDIUM (7) | Potential heap based buffer overflow in ParseJSS in VideoLAN VLC before 2.2.5 due to skipping NULL terminator in an input string allows attackers to execute arbitrary code via a crafted subtitles file. | 0 | 0 | NETWORK |
| CVE‑2017‑8310 | 2017‑05‑23 21:29:00 | MEDIUM (4) | Heap out-of-bound read in CreateHtmlSubtitle in VideoLAN VLC 2.2.x due to missing check of string termination allows attackers to read data beyond allocated memory and potentially crash the process (causing a denial of service) via a crafted subtitles file. | 0 | 0 | NETWORK |
| CVE‑2017‑17670 | 2017‑12‑15 09:29:00 | MEDIUM (7) | In VideoLAN VLC media player through 2.2.8, there is a type conversion vulnerability in modules/demux/mp4/libmp4.c in the MP4 demux module leading to a invalid free, because the type of a box may be changed between a read operation and a free operation. | 0 | 0 | NETWORK |
| CVE‑2017‑10699 | 2017‑06‑30 13:29:00 | HIGH (8) | avcodec 2.2.x, as used in VideoLAN VLC media player 2.2.7-x before 2017-06-29, allows out-of-bounds heap memory write due to calling memcpy() with a wrong size, leading to a denial of service (application crash) or possibly code execution. | 0 | 0 | NETWORK |
| CVE‑2016‑5108 | 2016‑06‑08 15:00:04 | HIGH (8) | Buffer overflow in the DecodeAdpcmImaQT function in modules/codec/adpcm.c in VideoLAN VLC media player before 2.2.4 allows remote attackers to cause a denial of service (crash) or possibly execute arbitrary code via a crafted QuickTime IMA file. | 0 | 0 | NETWORK |
| CVE‑2016‑3941 | 2016‑04‑18 15:59:01 | MEDIUM (4) | Buffer overflow in the AStreamPeekStream function in input/stream.c in VideoLAN VLC media player before 2.2.0 allows remote attackers to cause a denial of service (crash) via a crafted wav file, related to "seek across EOF." | 0 | 0 | NETWORK |
| CVE‑2015‑5949 | 2015‑08‑25 17:59:05 | MEDIUM (7) | VideoLAN VLC media player 2.2.1 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a crafted 3GP file, which triggers the freeing of arbitrary pointers. | 0 | 0 | NETWORK |
| CVE‑2014‑9743 | 2015‑08‑17 15:59:00 | MEDIUM (4) | Cross-site scripting (XSS) vulnerability in the httpd_HtmlError function in network/httpd.c in the web interface in VideoLAN VLC Media Player before 2.2.0 allows remote attackers to inject arbitrary web script or HTML via the path info. | 0 | 0 | NETWORK |
| CVE‑2014‑9630 | 2020‑01‑24 22:15:13 | HIGH (8) | The rtp_packetize_xiph_config function in modules/stream_out/rtpfmt.c in VideoLAN VLC media player before 2.1.6 uses a stack-allocation approach with a size determined by arbitrary input data, which allows remote attackers to cause a denial of service (memory corruption) or possibly have unspecified other impact via a crafted length value. | 2 | 6 | LOCAL |
| CVE‑2014‑9629 | 2020‑01‑24 22:15:13 | HIGH (8) | Integer overflow in the Encode function in modules/codec/schroedinger.c in VideoLAN VLC media player before 2.1.6 and 2.2.x before 2.2.1 allows remote attackers to conduct buffer overflow attacks and execute arbitrary code via a crafted length value. | 2 | 6 | LOCAL |
| CVE‑2014‑9628 | 2020‑01‑24 22:15:13 | HIGH (8) | The MP4_ReadBox_String function in modules/demux/mp4/libmp4.c in VideoLAN VLC media player before 2.1.6 allows remote attackers to trigger an unintended zero-size malloc and conduct buffer overflow attacks, and consequently execute arbitrary code, via a box size of 7. | 2 | 6 | LOCAL |
| CVE‑2014‑9627 | 2020‑01‑24 22:15:12 | HIGH (8) | The MP4_ReadBox_String function in modules/demux/mp4/libmp4.c in VideoLAN VLC media player before 2.1.6 performs an incorrect cast operation from a 64-bit integer to a 32-bit integer, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via a large box size. | 2 | 6 | LOCAL |
| CVE‑2014‑9626 | 2020‑01‑24 22:15:12 | HIGH (8) | Integer underflow in the MP4_ReadBox_String function in modules/demux/mp4/libmp4.c in VideoLAN VLC media player before 2.1.6 allows remote attackers to cause a denial of service or possibly have unspecified other impact via a box size less than 7. | 2 | 6 | LOCAL |
| CVE‑2014‑9625 | 2020‑01‑24 22:15:12 | HIGH (8) | The GetUpdateFile function in misc/update.c in the Updater in VideoLAN VLC media player before 2.1.6 performs an incorrect cast operation from a 64-bit integer to a 32-bit integer, which allows remote attackers to conduct buffer overflow attacks and execute arbitrary code via a crafted update status file, aka an "integer truncation" vulnerability. | 2 | 6 | LOCAL |
| CVE‑2014‑9598 | 2015‑01‑21 15:17:10 | MEDIUM (7) | The picture_Release function in misc/picture.c in VideoLAN VLC media player 2.1.5 allows remote attackers to execute arbitrary code or cause a denial of service (write access violation) via a crafted M2V file. | 0 | 0 | NETWORK |
| CVE‑2014‑9597 | 2015‑01‑21 15:17:09 | MEDIUM (7) | The picture_pool_Delete function in misc/picture_pool.c in VideoLAN VLC media player 2.1.5 allows remote attackers to execute arbitrary code or cause a denial of service (DEP violation and application crash) via a crafted FLV file. | 0 | 0 | NETWORK |
| CVE‑2014‑3441 | 2014‑05‑14 19:55:13 | MEDIUM (4) | codec\libpng_plugin.dll in VideoLAN VLC Media Player 2.1.3 allows remote attackers to cause a denial of service (crash) via a crafted .png file, as demonstrated by a png in a .wave file. | 0 | 0 | NETWORK |
| CVE‑2014‑1684 | 2014‑03‑03 16:55:04 | MEDIUM (4) | The ASF_ReadObject_file_properties function in modules/demux/asf/libasf.c in the ASF Demuxer in VideoLAN VLC Media Player before 2.1.3 allows remote attackers to cause a denial of service (divide-by-zero error and crash) via a zero minimum and maximum data packet size in an ASF file. | 0 | 0 | NETWORK |
| CVE‑2013‑7340 | 2014‑03‑21 04:38:59 | MEDIUM (4) | VideoLAN VLC Media Player before 2.0.7 allows remote attackers to cause a denial of service (memory consumption) via a crafted playlist file. | 0 | 0 | NETWORK |
| CVE‑2013‑6934 | 2014‑01‑23 21:55:05 | HIGH (8) | The parseRTSPRequestString function in Live Networks Live555 Streaming Media 2013.11.26, as used in VideoLAN VLC Media Player, allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a space character at the beginning of an RTSP message, which triggers an integer underflow, infinite loop, and buffer overflow. NOTE: this vulnerability exists because of an incomplete fix for CVE-2013-6933. | 0 | 0 | NETWORK |
| CVE‑2013‑6283 | 2013‑10‑25 23:55:05 | HIGH (8) | VideoLAN VLC Media Player 2.0.8 and earlier allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a long string in a URL in a m3u file. | 0 | 0 | NETWORK |
| CVE‑2013‑4388 | 2013‑10‑11 22:55:40 | MEDIUM (7) | Buffer overflow in the mp4a packetizer (modules/packetizer/mpeg4audio.c) in VideoLAN VLC Media Player before 2.0.8 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via unspecified vectors. | 0 | 0 | NETWORK |
| CVE‑2013‑3565 | 2020‑01‑31 22:15:10 | MEDIUM (6) | Multiple cross-site scripting (XSS) vulnerabilities in the HTTP Interface in VideoLAN VLC Media Player before 2.0.7 allow remote attackers to inject arbitrary web script or HTML via the (1) command parameter to requests/vlm_cmd.xml, (2) dir parameter to requests/browse.xml, or (3) URI in a request, which is returned in an error message through share/lua/intf/http.lua. | 3 | 3 | NETWORK |
| CVE‑2013‑3564 | 2020‑02‑06 22:15:10 | MEDIUM (5) | The web interface in VideoLAN VLC media player before 2.0.7 has no access control which allows remote attackers to view directory listings via the 'dir' command or issue other commands without authenticating. | 4 | 1 | NETWORK |
| CVE‑2013‑3245 | 2013‑07‑10 19:55:05 | MEDIUM (6) | plugins/demux/libmkv_plugin.dll in VideoLAN VLC Media Player 2.0.7, and possibly other versions, allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a crafted MKV file, possibly involving an integer overflow and out-of-bounds read or heap-based buffer overflow, or an uncaught exception. NOTE: the vendor disputes the severity and claimed vulnerability type of this issue, stating "This PoC crashes VLC, indeed, but does nothing more... this is not an integer overflow error, but an uncaught exception and I doubt that it is exploitable. This uncaught exception makes VLC abort, not execute random code, on my Linux 64bits machine." A PoC posted by the original researcher shows signs of an attacker-controlled out-of-bounds read, but the affected instruction does not involve a register that directly influences control flow | 3 | 3 | NETWORK |
| CVE‑2013‑1954 | 2013‑07‑10 19:55:05 | MEDIUM (7) | The ASF Demuxer (modules/demux/asf/asf.c) in VideoLAN VLC media player 2.0.5 and earlier allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a crafted ASF movie that triggers an out-of-bounds read. | 0 | 0 | NETWORK |
| CVE‑2013‑1868 | 2013‑07‑10 19:55:05 | HIGH (9) | Multiple buffer overflows in VideoLAN VLC media player 2.0.4 and earlier allow remote attackers to cause a denial of service (crash) and execute arbitrary code via vectors related to the (1) freetype renderer and (2) HTML subtitle parser. | 0 | 0 | NETWORK |
| CVE‑2012‑5855 | 2013‑07‑10 19:55:01 | MEDIUM (4) | The SHAddToRecentDocs function in VideoLAN VLC media player 2.0.4 and earlier might allow user-assisted attackers to cause a denial of service (crash) via a crafted file name that triggers an incorrect string-length calculation when the file is added to VLC. NOTE: it is not clear whether this issue crosses privilege boundaries or whether it can be exploited without user interaction. | 0 | 0 | NETWORK |
| CVE‑2012‑5470 | 2012‑10‑26 10:39:17 | MEDIUM (4) | libpng_plugin in VideoLAN VLC media player 2.0.3 allows remote attackers to cause a denial of service (application crash) via a crafted PNG file. | 0 | 0 | NETWORK |
| CVE‑2012‑3377 | 2012‑07‑12 21:55:08 | MEDIUM (7) | Heap-based buffer overflow in the Ogg_DecodePacket function in the OGG demuxer (modules/demux/ogg.c) in VideoLAN VLC media player before 2.0.2 allows remote attackers to cause a denial of service (application crash) and possibly execute arbitrary code via a crafted OGG file. | 0 | 0 | NETWORK |
| CVE‑2012‑2396 | 2012‑04‑19 21:55:01 | MEDIUM (4) | VideoLAN VLC media player 2.0.1 allows remote attackers to cause a denial of service (divide-by-zero error and application crash) via a crafted MP4 file. | 0 | 0 | NETWORK |
| CVE‑2012‑1776 | 2012‑03‑19 16:55:01 | HIGH (9) | Multiple heap-based buffer overflows in VideoLAN VLC media player before 2.0.1 allow remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted Real RTSP stream. | 0 | 0 | NETWORK |
| CVE‑2012‑1775 | 2012‑03‑19 16:55:01 | HIGH (9) | Stack-based buffer overflow in VideoLAN VLC media player before 2.0.1 allows remote attackers to execute arbitrary code via a crafted MMS:// stream. | 0 | 0 | NETWORK |
| CVE‑2012‑0904 | 2012‑01‑20 17:55:03 | MEDIUM (4) | VLC media player 1.1.11 allows remote attackers to cause a denial of service (crash) via a long string in an amr file. | 0 | 0 | NETWORK |
| CVE‑2012‑0023 | 2012‑10‑30 19:55:04 | HIGH (9) | Double free vulnerability in the get_chunk_header function in modules/demux/ty.c in VideoLAN VLC media player 0.9.0 through 1.1.12 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via a crafted TiVo (TY) file. | 0 | 0 | NETWORK |
| CVE‑2011‑3623 | 2014‑12‑26 20:59:08 | HIGH (8) | Multiple stack-based buffer overflows in VideoLAN VLC media player before 1.0.2 allow remote attackers to execute arbitrary code via (1) a crafted ASF file, related to the ASF_ObjectDumpDebug function in modules/demux/asf/libasf.c; (2) a crafted AVI file, related to the AVI_ChunkDumpDebug_level function in modules/demux/avi/libavi.c; or (3) a crafted MP4 file, related to the __MP4_BoxDumpStructure function in modules/demux/mp4/libmp4.c. | 0 | 0 | NETWORK |
| CVE‑2011‑2588 | 2011‑07‑27 02:55:02 | MEDIUM (7) | Heap-based buffer overflow in the AVI_ChunkRead_strf function in libavi.c in the AVI demuxer in VideoLAN VLC media player before 1.1.11 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted AVI media file. | 0 | 0 | NETWORK |
| CVE‑2011‑2587 | 2011‑07‑27 02:55:02 | MEDIUM (7) | Heap-based buffer overflow in the DemuxAudioSipr function in real.c in the RealMedia demuxer in VideoLAN VLC media player 1.1.x before 1.1.11 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted Real Media file. | 0 | 0 | NETWORK |
| CVE‑2011‑2194 | 2011‑06‑24 20:55:04 | HIGH (9) | Integer overflow in the XSPF playlist parser in VideoLAN VLC media player 0.8.5 through 1.1.9 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via unspecified vectors that trigger a heap-based buffer overflow. | 0 | 0 | NETWORK |
| CVE‑2011‑1931 | 2011‑07‑07 21:55:02 | MEDIUM (7) | sp5xdec.c in the Sunplus SP5X JPEG decoder in libavcodec in FFmpeg before 0.6.3 and libav through 0.6.2, as used in VideoLAN VLC media player 1.1.9 and earlier and other products, performs a write operation outside the bounds of an unspecified array, which allows remote attackers to cause a denial of service (memory corruption) or possibly execute arbitrary code via a malformed AMV file. | 0 | 0 | NETWORK |
| CVE‑2011‑1684 | 2011‑05‑03 20:55:12 | MEDIUM (7) | Heap-based buffer overflow in the MP4_ReadBox_skcr function in libmp4.c in the MP4 demultiplexer in VideoLAN VLC media player 1.x before 1.1.9 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted MP4 file. | 0 | 0 | NETWORK |
| CVE‑2011‑1087 | 2011‑05‑03 19:55:04 | HIGH (8) | Buffer overflow in VideoLAN VLC media player 1.0.5 allows user-assisted remote attackers to cause a denial of service (memory corruption and application crash) or possibly execute arbitrary code via a crafted .mp3 file that is played during bookmark creation. | 0 | 0 | NETWORK |
| CVE‑2011‑0531 | 2011‑02‑07 21:00:17 | HIGH (9) | demux/mkv/mkv.hpp in the MKV demuxer plugin in VideoLAN VLC media player 1.1.6.1 and earlier allows remote attackers to cause a denial of service (crash) and execute arbitrary commands via a crafted MKV (WebM or Matroska) file that triggers memory corruption, related to "class mismatching" and the MKV_IS_ID macro. | 0 | 0 | NETWORK |
| CVE‑2011‑0522 | 2011‑02‑07 21:00:15 | MEDIUM (7) | The StripTags function in (1) the USF decoder (modules/codec/subtitles/subsdec.c) and (2) the Text decoder (modules/codec/subtitles/subsusf.c) in VideoLAN VLC Media Player 1.1 before 1.1.6-rc allows remote attackers to execute arbitrary code via a subtitle with an opening "<" without a closing ">" in an MKV file, which triggers heap memory corruption, as demonstrated using refined-australia-blu720p-sample.mkv. | 0 | 0 | NETWORK |
| CVE‑2011‑0021 | 2011‑01‑25 19:00:04 | HIGH (9) | Multiple heap-based buffer overflows in cdg.c in the CDG decoder in VideoLAN VLC Media Player before 1.1.6 allow remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted CDG video. | 0 | 0 | NETWORK |
| CVE‑2010‑3907 | 2011‑01‑03 20:00:43 | HIGH (9) | Multiple integer overflows in real.c in the Real demuxer plugin in VideoLAN VLC Media Player before 1.1.6 allow remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a zero i_subpackets value in a Real Media file, leading to a heap-based buffer overflow. | 0 | 0 | NETWORK |
| CVE‑2010‑3276 | 2011‑03‑28 16:55:03 | HIGH (9) | libdirectx_plugin.dll in VideoLAN VLC Media Player before 1.1.8 allows remote attackers to execute arbitrary code via a crafted width in an NSV file. | 0 | 0 | NETWORK |
| CVE‑2010‑3275 | 2011‑03‑28 16:55:03 | HIGH (9) | libdirectx_plugin.dll in VideoLAN VLC Media Player before 1.1.8 allows remote attackers to execute arbitrary code via a crafted width in an AMV file, related to a "dangling pointer vulnerability." | 0 | 0 | NETWORK |
| CVE‑2010‑3124 | 2010‑08‑26 18:36:36 | HIGH (9) | Untrusted search path vulnerability in bin/winvlc.c in VLC Media Player 1.1.3 and earlier allows local users, and possibly remote attackers, to execute arbitrary code and conduct DLL hijacking attacks via a Trojan horse wintab32.dll that is located in the same folder as a .mp3 file. | 0 | 0 | NETWORK |
| CVE‑2010‑2937 | 2010‑08‑20 18:00:02 | MEDIUM (5) | The ReadMetaFromId3v2 function in taglib.cpp in the TagLib plugin in VideoLAN VLC media player 0.9.0 through 1.1.2 does not properly process ID3v2 tags, which allows remote attackers to cause a denial of service (application crash) via a crafted media file. | 0 | 0 | NETWORK |
| CVE‑2010‑2062 | 2014‑12‑26 20:59:07 | HIGH (8) | Integer underflow in the real_get_rdt_chunk function in real.c, as used in modules/access/rtsp/real.c in VideoLAN VLC media player before 1.0.1 and stream/realrtsp/real.c in MPlayer before r29447, allows remote attackers to execute arbitrary code via a crafted length value in an RDT chunk header. | 0 | 0 | NETWORK |
| CVE‑2010‑1445 | 2014‑12‑26 20:59:06 | HIGH (8) | Heap-based buffer overflow in VideoLAN VLC media player before 1.0.6 allows remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted byte stream in an RTMP session. | 0 | 0 | NETWORK |
| CVE‑2010‑1444 | 2014‑12‑26 20:59:06 | HIGH (8) | The ZIP archive decompressor in VideoLAN VLC media player before 1.0.6 allows remote attackers to cause a denial of service (invalid memory access and application crash) or possibly execute arbitrary code via a crafted archive. | 0 | 0 | NETWORK |
| CVE‑2010‑1443 | 2014‑12‑26 20:59:04 | MEDIUM (5) | The parse_track_node function in modules/demux/playlist/xspf.c in the XSPF playlist parser in VideoLAN VLC media player before 1.0.6 allows remote attackers to cause a denial of service (NULL pointer dereference and application crash) via an empty location element in an XML Shareable Playlist Format (XSPF) document. | 0 | 0 | NETWORK |
| CVE‑2010‑1442 | 2014‑12‑26 20:59:03 | HIGH (8) | VideoLAN VLC media player before 1.0.6 allows remote attackers to cause a denial of service (invalid memory access and application crash) or possibly execute arbitrary code via a crafted byte stream to the (1) AVI, (2) ASF, or (3) Matroska (aka MKV) demuxer. | 0 | 0 | NETWORK |
| CVE‑2010‑1441 | 2014‑12‑26 20:59:00 | HIGH (8) | Multiple heap-based buffer overflows in VideoLAN VLC media player before 1.0.6 allow remote attackers to cause a denial of service (application crash) or possibly execute arbitrary code via a crafted byte stream to the (1) A/52, (2) DTS, or (3) MPEG Audio decoder. | 0 | 0 | NETWORK |
| CVE‑2010‑0364 | 2010‑01‑21 20:30:00 | HIGH (9) | Stack-based buffer overflow in VideoLAN VLC Media Player 0.8.6 allows user-assisted remote attackers to execute arbitrary code via an ogg file with a crafted Advanced SubStation Alpha Subtitle (.ass) file, probably involving the Dialogue field. | 0 | 0 | NETWORK |

Get the IT stuff done that nobody wants to do.
Patch more applications, achieve compliance, and prevent problems while reducing stress with Lavawall®.
Security First
A security tool by security auditors. From Passkeys and Argon2i to source validation and MVSP principles, Lavawall® has you covered.
Constant Improvement
More features and more security added nearly every day.
More patchable programs added every week
While Ninite and other patching tools have had the same patch offerings for decades, we're monitoring stats to keep adding the most useful programs (currently over 7,438)!
Details matter
From wrapping TLS communications in extra encryption and uninstalling remote support tools when they aren't used to detailed statistical analysis of system and network performance, Lavawall® goes in-depth.
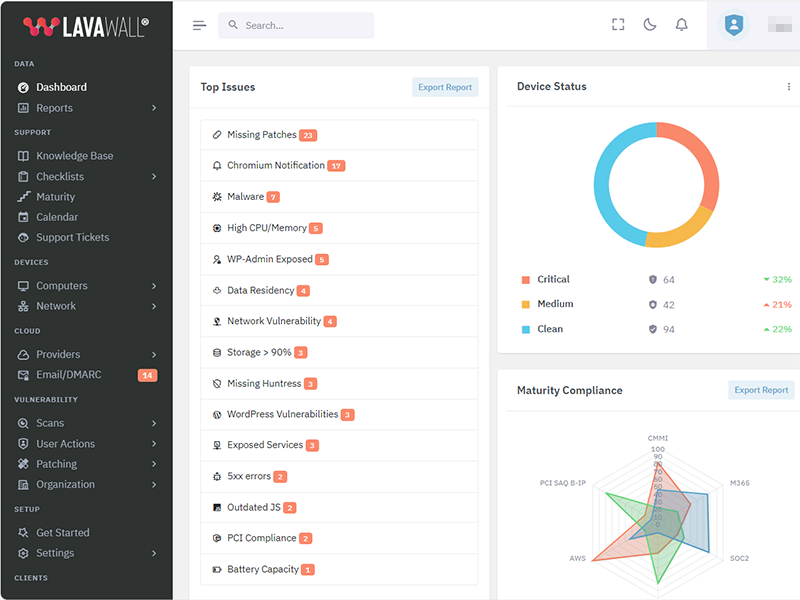
System Reliability
Monitor battery, disk, and process health. Lavawall® combines system health, age, operating system support, memory levels, and other attributes to prioritize systems for replacement.
Human and automated support
Get immediate fixes, user notifications, admin notifications -- and even security-certified human level 3 support when our advanced statistical analysis confirms a problem or anomaly.
| 2025‑03‑27 | 0.12.64.251 | Add efficiency to package management system |
| 2025‑03‑10 | 0.12.60.247 | |
| 2025‑03‑04 | 0.12.58.245 | |
| 2025‑03‑03 | 0.12.57.244 | Add TPM complience check and ensure consistent memory gathering in windows/linux/mac |
| 2025‑02‑28 | 0.12.56.243 | Windows RAM reporting and persistent scalability framework enhancements |
| 2025‑02‑27 | 0.12.55.242 | Battery health refinements |
| 2025‑02‑26 | 0.12.54.241 | Add battery health statistics |
| 2025‑02‑26 | 0.12.53.240 | |
| 2025‑01‑29 | 0.12.35.222 | Risk score refinements |
| 2025‑01‑17 | 0.12.29.216 | Enhanced compliance and non-standard AV |
| 2025‑01‑13 | 0.12.28.215 | Improved process graphs |
| 2025‑01‑07 | 0.12.27.214 | Antivirus details, compliance |
| 2024‑12‑27 | 0.12.24.211 | |
| 2024‑12‑02 | 0.12.19.206 | |
| 2024‑11‑22 | 0.12.18.205 | |
| 2024‑10‑30 | 0.12.8.195 | Mac update refinements |
| 2024‑10‑25 | 0.12.3.190 | |
| 2024‑10‑21 | 0.12.0.187 | Macos implementaiton, linux and windows improvements |
| 2024‑10‑16 | 0.11.128.186 | Linux stats and system information improvements, improvements for application shutdown |
| 2024‑09‑12 | 0.11.113.171 | CPU Optimizations and Packages reliability improvements |
| 2024‑09‑05 | 0.11.106.164 | Phased deployment enhancements |
| 2024‑09‑04 | 0.11.103.161 | |
| 2024‑09‑02 | 0.11.102.160 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑30 | 0.11.99.157 | CPU Optimizations and Packages reliability improvements |
| 2024‑08‑29 | 0.11.98.156 | CPU utilization and console event optimization |
| 2024‑08‑28 | 0.11.97.155 | Reliability to detect unusual updates like redistributables. |
| 2024‑08‑27 | 0.11.96.154 | |
| 2024‑08‑26 | 0.11.95.153 | Faster response for reboot requests |
| 2024‑08‑20 | 0.11.92.150 | Additional package upgrade pre-requisites |
| 2024‑08‑15 | 0.11.89.147 | |
| 2024‑08‑06 | 0.11.87.145 | |
| 2024‑07‑26 | 0.11.83.141 | Add resiliency for MAC duplicates and uptime |
| 2024‑07‑25 | 0.11.82.140 | Changes to facilitate cross-platform use. Bitlocker and Windows key refinements |
| 2024‑07‑15 | 0.11.80.138 | Antivirus and temperature added to configuration checks |
| 2024‑07‑15 | 0.11.79.137 | Add configuration checks for execution policy and secure boot |
| 2024‑07‑11 | 0.11.77.135 | load balancing refinements |
| 2024‑07‑10 | 0.11.76.134 | Add additional load balancing and data residency capabilities, add randomness to recurring task timings to decrease server load |
| 2024‑07‑05 | 0.11.74.132 | changes to graph and residual work on user imporsonation |
| 2024‑07‑04 | 0.11.73.131 | Add configuration checks for execution policy and secure boot. |
| 2024‑07‑03 | 0.11.72.130 | Enhanced event log monitoring |
| 2024‑07‑02 | 0.11.71.129 | Add details to Windows updates, enhanced risk metrics for application patches |
| 2024‑06‑19 | 0.11.65.123 | Update resiliancy and garbage collection |
| 2024‑06‑13 | 0.11.60.118 | Enhanced logging |
| 2024‑06‑12 | 0.11.55.113 | Include the primary drive serial number; MAC addresses for built-in wireless, Bluetooth, and ethernet into the device hash to restore uninstalled and reinstalled devices in cases where the motherboard serial is not unique |
| 2024‑06‑07 | 0.11.54.112 | Patch and package uninstall data addition |
| 2024‑06‑05 | 0.11.47.105 | refine per-user registry application listing |
| 2024‑06‑02 | 0.11.45.103 | uninstall and reinstall refinements, refine local logging, refine self-update and uninstall timing |
| 2024‑05‑30 | 0.11.21.79 | various bug fixes and improvements |
| 2024‑05‑28 | 0.11.16.74 | Error logging, registration, and uninstall improvements. |
| 2024‑05‑24 | 0.11.14.72 | applied changes for devices and login commands, changes for registration as well |
NOTE: changes after June 2024 are incorportated into the Windows Changelog as the codebases for Windows, Linux, and Mac were combined
| 2024‑05‑20 | 253 | Added cleanup of old .json files during a re-install |
| 2024‑05‑13 | 252 | Added apt-get update to install |
| 2024‑05‑06 | 248 | Allow restart to use /var/run/reboot-required if needrestart is not installed |
| 2024‑04‑22 | 239 | Improve internal update and version tracking |
| 2024‑04‑15 | 235 | Add support for Yum packages |
| 2024‑04‑08 | 233 | Align patching with Windows patch reporting |
| 2024‑04‑02 | 228 | Add support for needrestart |
| 2024‑03‑04 | 224 | Schedule restarts |
| 2024‑03‑25 | 221 | Add support for apt packages |
| 2024‑03‑18 | 212 | Implement release management |
| 2024‑03‑11 | 202 | Add user login monitoring |
| 2024‑03‑04 | 189 | Enhance installation reliability |
| 2024‑02‑26 | 187 | Exapand triggers to identify if the instance needs to be restarted |
| 2024‑02‑19 | 146 | Improve compatibility for non-AWS instances |
| 2024‑02‑14 | 138 | Add self-uninstall capabilities |
| 2024‑02‑12 | 135 | Enhance scheduling flexibility |
| 2024‑02‑07 | 132 | Add kernel version tracking |
| 2024‑02‑05 | 124 | Add device hash to cryptographic self-update script validation |
| 2024‑01‑29 | 107 | Enhance encryption of patch data |
| 2024‑01‑22 | 98 | Improve how available storage is calculated |
| 2024‑01‑15 | 97 | Move initial tasks from installation file to sub scripts |
| 2024‑05‑21 | 91 | Improve multi-distribution compatibility |
| 2024‑05‑21 | 79 | Improve encryption reliability |
| 2023‑12‑11 | 68 | Enhance cryptographic validation of new scripts before updating |
| 2023‑11‑20 | 62 | Add inner layer of AES encryption in case TLS inspection doesn't allow for a secure connection |
| 2023‑11‑27 | 56 | Additional base cases for resiliancy |
| 2023‑11‑20 | 54 | Additional headers added to authentication process during installation. |
| 2023‑11‑20 | 53 | Enhanced key management |
| 2023‑11‑15 | 51 | Add insecure installation parameter to allow installation in environments with TLS inspection or other machine-in-the-middle situations. |
| 2023‑11‑06 | 42 | Enhance redundant encryption during installation. |
| 2023‑10‑30 | 33 | Improve install-over compatibility |
| 2023‑10‑23 | 18 | Add reboot configuration and scheduling |
| 2023‑10‑23 | 17 | Add self-updating functionality. |
| 2023‑10‑16 | 15 | Add Linux patching information for apt |
| 2023‑10‑09 | 14 | Collect system information |
| 2023‑10‑09 | 13 | Add Linux distribution information |
| 2023‑09‑30 | 12 | Add memory monitoring |
| 2023‑09‑30 | 10 | Add hardware information |
| 2023‑09‑23 | 9 | Add AWS information |
| 2023‑09‑23 | 8 | Add customized schedule capability for configuration updates |
| 2023‑09‑23 | 7 | Add support for package monitoring using package and dpkg logs |
| 2023‑09‑16 | 6 | Add storage data configuration gathering |
| 2023‑09‑16 | 5 | Add CPU information |
Lavawall® was built from the ground up with these concerns and the Minimum Viable Secure Product requirements in mind.
Some of the controls we implemented include:
- PassKeys as the preferred primary authentication at no additional cost
- Single Sign-on using modern, maintained, and industry-standard protocols for all customers at no additional cost
- Multi-Factor Authentication as a non-negotiable default
- Encrypting communications the same way as TLS again within the TLS tunnel, so we can allow TLS inspection without breaking like Huntress or disclosing security vulnerabilities to eavesdroppers.
- Encouraging external vulnerability reports and customer testing
- Passwords checked against popular disclosed passwords, hashed before they leave your computer, and then stored using Argon2id
- Not requiring the use of passwords at all. We consider them a temporary backup authentication in case you can't use passkeys or SSO.
Lavawall® databases and front-end systems are hosted with AWS in Montréal, Québec, Canada.
We send emails through AWS in Ireland and dedicated servers in Calgary, Alberta, Canada.
We send text messages for additional identity verification through Twilio in the United States.
We store executables and pass requests through Cloudflare at your nearest edge location.
We use Cloudflare for risk management, turnstile, and web application firewall services.
We use LeadPages for landing pages.
We use Google and Facebook for analytics on our public-facing pages, but they do not have access to the console.
We integrate with third-party tools, such as Microsoft, Google, Huntress, Screen Connect, Axcient, and Datto in their respective locations. However, you must initiate these integrations through single sign-on or by enabling them in your Lavawall® console.
Active security by design
Lavawall® is under active development with the latest release including:
7,438+
Monitored Applications
61+
System Metrics
Actively manage your IT with Lavawall®
Patching
Updates Beyond Windows
Lavawall® prevents the 80% of breaches and failed audits due to missing patches and updates.
You can reduce application patching delays from 67 days to nearly immediate with the 7,438+ applications that Lavawall® monitors and patches.
Patch release monitoring
Monitor everything without having to select packages or “managed applications”
Patch impact classification
Standard and optional Windows patches
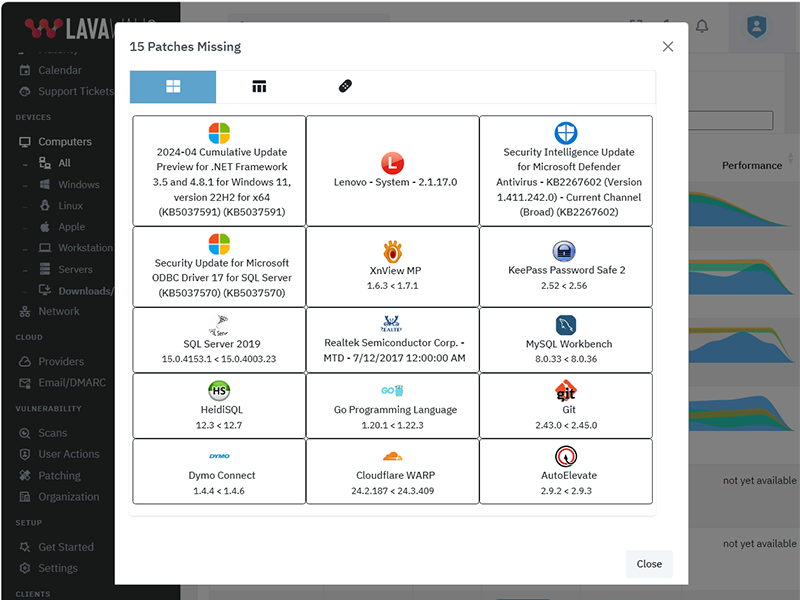
Application Patching
Some of the applications that Lavawall® monitors and audits include:
Logos are property of their respective trademark holders and are not affiliated with ThreeShield or Lavawall. We have not audited the security of most of the listed tools.
The above listing includes products that Lavawall® monitors through public information and/or proprietary statistical analysis.
Although we do have a partner relationship with some of the listed products and companies, they do not necessarily endorse Lavawall® or have integrations with our systems.
Learn More
Flexible Term; Flexible Service
Flexibility for your dynamic business
You need to get your arms around compliance and security and don't want to get locked into “high watermark” monthly invoices or multi-year contracts.
Pay-as-you-need monthly pricing
DIY, full management, and coaching options
Choose the plan that's right for you
Simple pricing. No hidden fees. Advanced features for you business.
Month
Annual
Get 2 months free with Annual!
Minimal
Pay-as-you go. No Commitments.
C$3.25 /computer/Month
C$32.50 /computer/Year
-
1 computer
or 1 of the following cloud integrations:
AWS, Axcient, Datto, Google, Huntress, M365, Sophos Central integrations
(each integration counts as 1 computer) -
50+ application patches
-
30-day Logs
-
Security configuration monitoring
-
Lavawall® support
-
Domain Scanning: C$20/domainDomain Scanning: C$200/domain
-
Level 3+ IT support for IT
-
IT coaching sessions
-
Automatic discount and upgrade to Business Standard at 77 devices
Business Standard
Basic services with 90-day logs
C$250 /Month
C$2,250 /Year
-
150 computers
Additional computers: C$2.50/computerAdditional computers: C$25/computer -
25 domains
Additional domains: C$15/domainAdditional domains: C$150/domain -
AWS, Axcient, Datto, Google, Huntress, M365, Sophos Central integrations
-
7,438+ application patch monitoring
-
90-day Logs
-
Security configuration monitoring
-
Lavawall® support
-
Level 3+ IT support for IT
-
IT coaching sessions
-
Automatic discount and upgrade to Full Service at 950 devices
Full Service
Optimize & audit-ready your IT
$2,250 /Month
$22,500 /Year
-
1,500 computers included
Additional computers: C$2/computerAdditional computers: C$20/computer -
125 domains included
Additional domains: C$10/domainAdditional domains: C$100/domain -
AWS, Axcient, Datto, Google, Huntress, M365, Sophos Central integrations
-
7,438+ application patch monitoring
-
365-day Logs
-
Security configuration monitoring
-
Lavawall® support
-
L3 IT support for IT
-
IT coaching sessions
Frequently Asked Questions
If you can not find answer to your question in our FAQ, you can always contact us or email us. We will answer you shortly!
General Questions
- Two years after a missing Plex Media Server led to the LastPass breach, the
Remote Monitorign and Management (RMM) tools availabel for Manged IT Service Providers (MSPs)
still didn't monitor for it.
Going through industry-specific applications, we noticed many were missing from the big RMM and patching providers. MSPs, insurance providers, and organizations that put their cleints at risk need to know about these risks, which lead to the largest number of critical audit findings and breaches - After 20 years of writing the same audit findings about system configurations, Payment Card Industry (PCI) compliance, and missing patches, our technical co-founder wanted to make it easier fo avoid these findings
- The existing risk visibility tools for insurance underwriters took a shallow look at Internet-facing risks. They -- along with all businesses -- need a deeper view of the threats that could actually lead to breaches.
- Domain risks
- Operating System (OS) patches
- Application patches
- Network vulnerabilities
- Cloud vulnerabilities
- OS configurations
You can use your own logo for the console and notifications. You can also use a CNAME to automatically brand your console.
Note: you cannot currently re-proxy the CNAME to Lavawall® through Cloudflare.
Lavawall® supports the following operating systems:
Lavawall® does not currently support non systemd distributions, such as Devuan, Artix Linux, PCLinuxOS, OpenWRT, and DD-WRT. However, we will support them by the end of 2024.
In June 2024, we combined the Windows and Linux systems for a consistent experience. This added support for RedHat and MacOS.
Privacy & Security
However, we do allow passwords and use passwords as part of the zero-knowledge encryption for your clients' sensitive data, such as Bitlocker keys and Personally-Identifiable Information (PII).
These passwords use Argon2id slow hashes with individual salts and peppers. They go through a few hash rounds on your computer before being sent to our servers for further hashing.
We have added an additional secure tunnel that mimics the TLS process within the public TLS tunnel. This extra tunnel provides authentication and privacy for the workstations and the Lavawall® servers to prevent attacks such as the one that took down Solar Winds.
Remote access is not enabled for read-only and audit situations.
Get In Touch
Have a quick question and don't want to talk? Send us a quick note with the form below and we'll reply within one business day.
NW Calgary:
ThreeShield Information Security Corporation
600 Crowfoot Crescent N.W., Suite 340
Calgary, Alberta
T3G 0B4
SE Calgary:
ThreeShield Information Security Corporation
105, 11500 - 29th St. SE
Calgary, Alberta
T2Z 3W9
Canada