Peace of Mind
After a ransomware attack, people are rightfully concerned that they missed a delayed instance that is going to start the whole mess all over again.Antivirus, EDR, and breach detection tools usually only check for known executables and behaviour while ransomware is running. However, they don't do an in-depth examination to look for pre-warning signs.
The Lavawall® Akira Ransomware Hunter is a quick scan of your computers to look for these signs. Some of these indicators of compromise include:
- Suspicious executable files.
- Malicious commands that were recently run.
- Ransom notes (we initially focused on Akira, but now include ransom notes from the most common ransomware variants).
- Partially and fully-encrypted files.
- Exfiltration tools to steal your data before encrypting it as part of hybrid ransomware attacks.
- Suspicious programs that were recently run.
- Newly-installed services.
- Changes to scheduled tasks.
- Changes to administrator accounts.
- Archives that were being staged prior to encryption.
- Executables that were getting ready to run.
- RMMs and other remote support tools that hackers use for remote access.
- Programs set to run automatically on boot or login.
- Account group changes
- User changes
One of the first things that hackers do when they gain access is install remote access tools to maintain their access.
The ransomware hunter analyzes installed remote access tools, data exfiltration tools, and suspicious processes that hackers use to perform “living off the land” attacks.
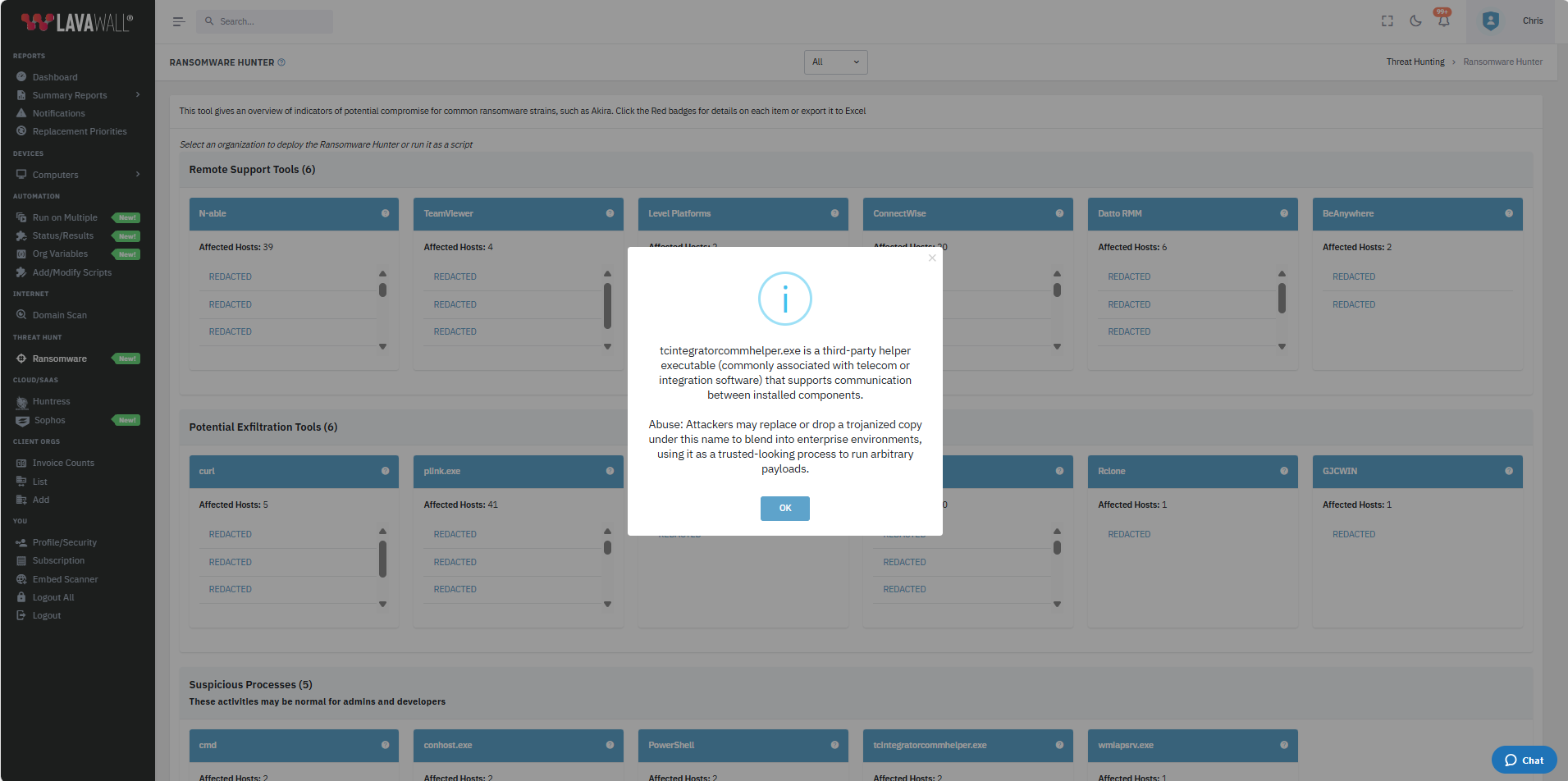
When a tool comes up that you're not familiar with, just click the question mark in the computer listing's header for a quick explanation.
If you'd like to discuss it with one of our Level 3 Cybersecurity experts, click the Chat button and a human expert will be happy to discuss it with you.
You can also always call us. Remember that although Lavawall® automates most of our security work, it’s just one of the many ways that ThreeShield provides advanced security support to our MSP partners and we’re always available to resolve issues or expand Lavawall®’s capabilities.
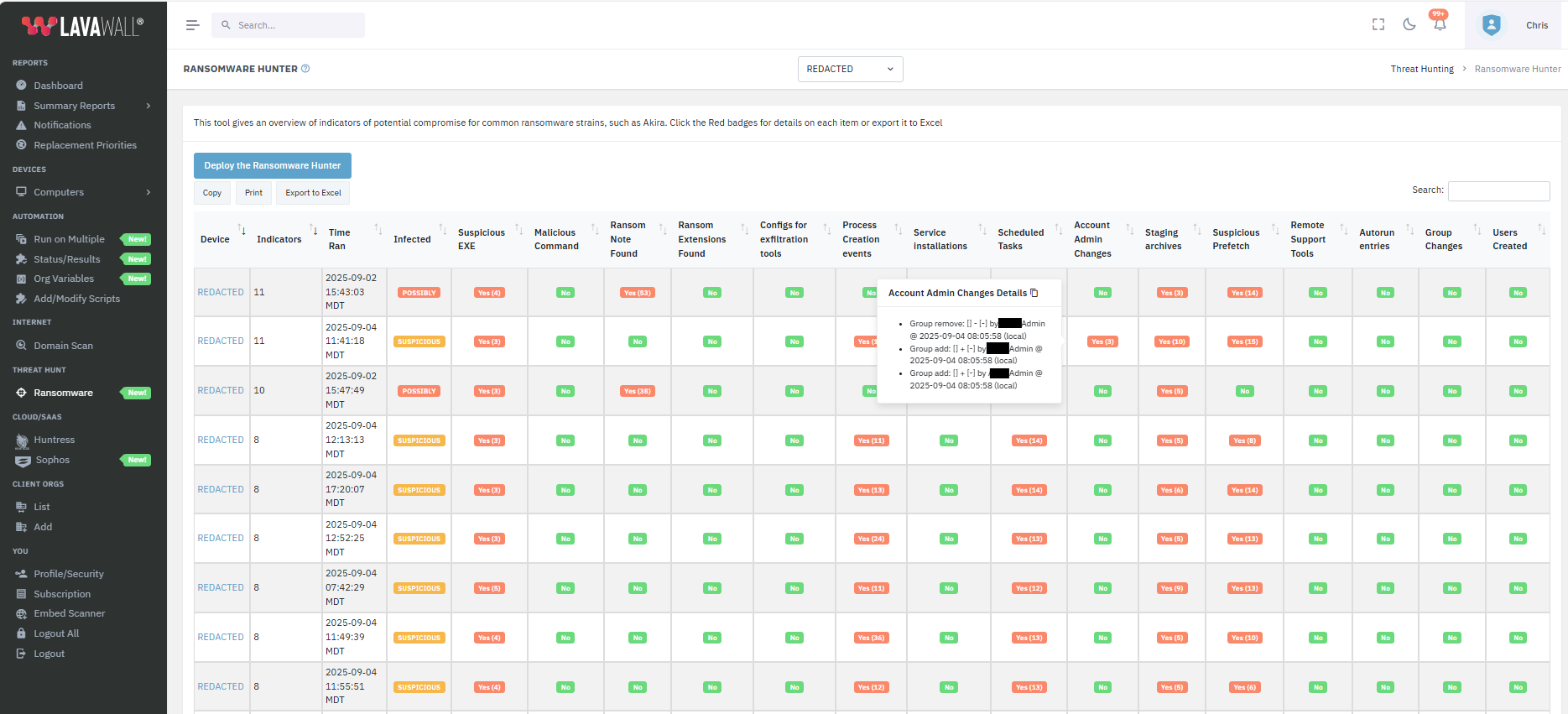
The summary view shows a count of what was found. You can click any of the red badges to see the details
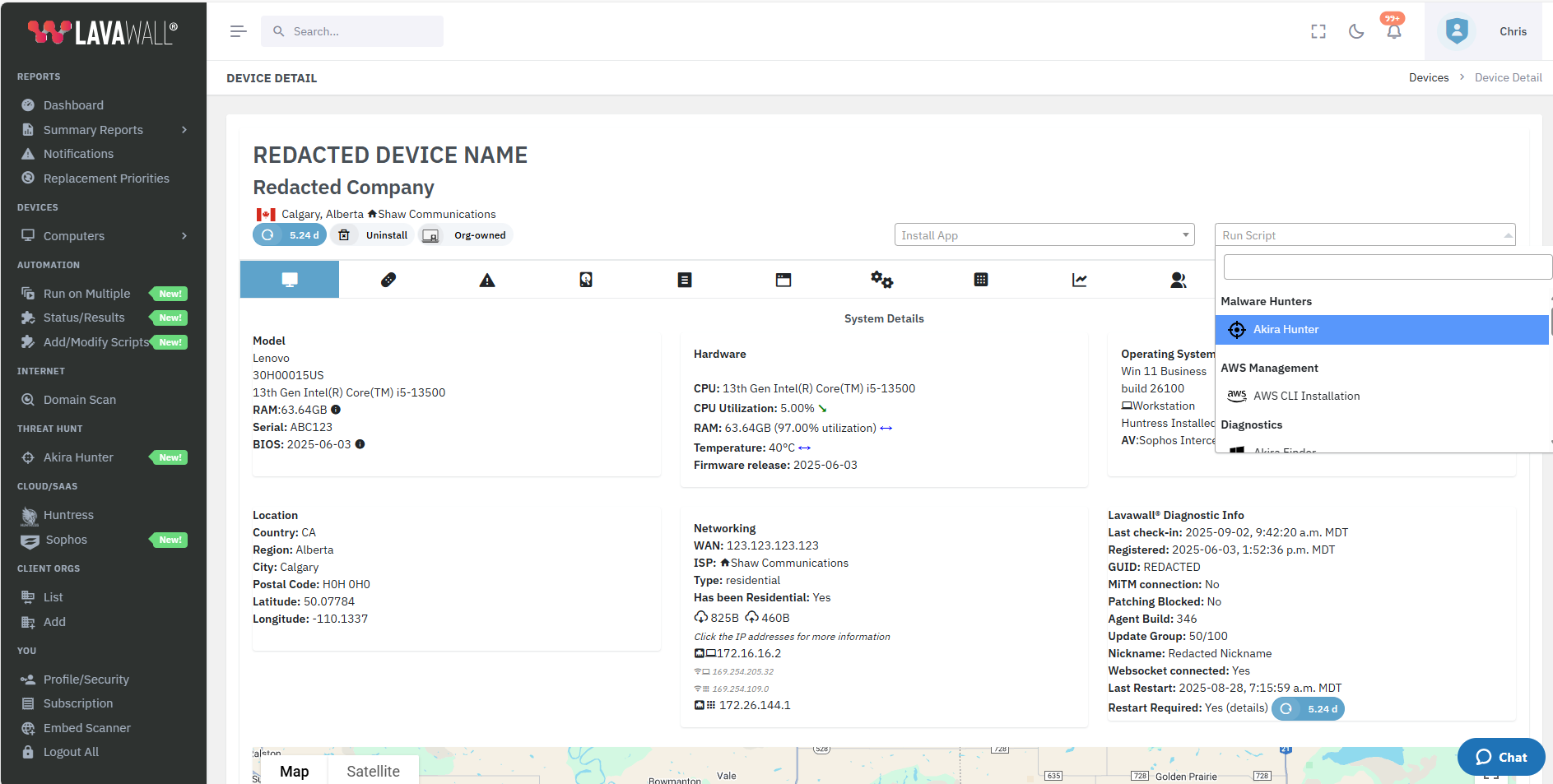
Easy Deployment
You can deploy the Akira Hunter by selecting an organization from the organization drop-down in the Akira Hunter summary page and then clicking Deploy the Akira Hunter.You can also install it using the Run Script searchable drop down in device details
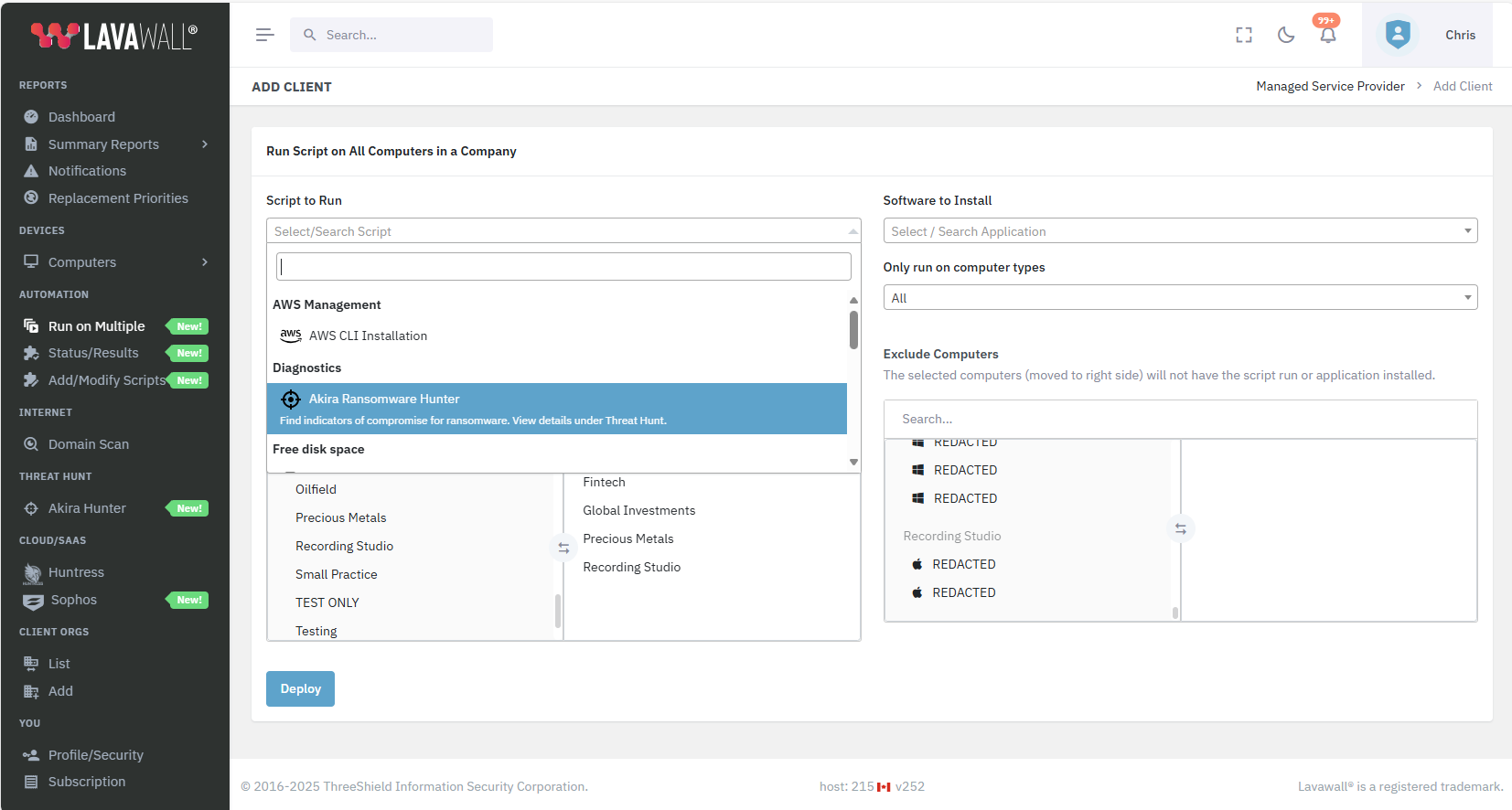
You can also deploy it to multiple companies or computers types
The summary view shows a count of what was found. You can click any of the red badges to see the details
The Lavawall® Ransomware Hunter is also part of Lavawall®'s regular health scans, which run once per month by default.
The Ransomware Hunter takes 5-15 minutes to run and update the summary on a typical computer.
If you have any questions or need further assistance, feel free to reach out through our chat, phone or email on our contact page!